Data Enrichment, People Data Labs and Another 622M Email Addresses
Troy Hunt
NOVEMBER 22, 2019
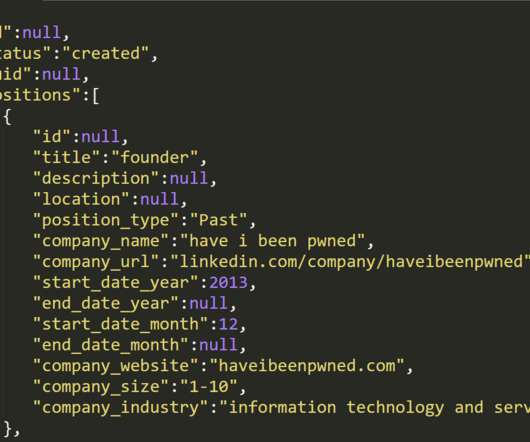
"id":null, "title":"partner", "description":null, "location":null, "position_type":"Past", "company_name":"report uri", "company_url":"linkedin.com/company/report-uri", "start_date_year":2017, "end_date_year":null, "start_date_month":11, "end_date_month":null, "company_website":null, "company_size":"1-10", "company_industry":"internet" }, {. "id":null,


















Let's personalize your content