Infosec policy development
Notice Bored
APRIL 10, 2021
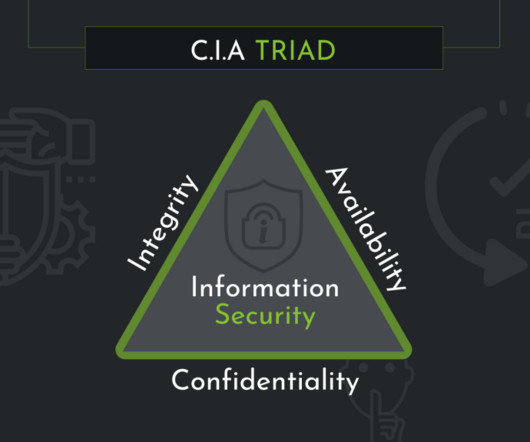
We're currently preparing some new information risk and security policies for SecAware.com. This policy will outline the associated information risks, mitigating controls and other relevant approaches. How does this relate to penetration testing, incident management and assurance? How should issues be addressed?
































Let's personalize your content