Critical Infrastructure at Risk from New Vulnerabilities Found in Wireless IIoT Devices
The Hacker News
FEBRUARY 9, 2023
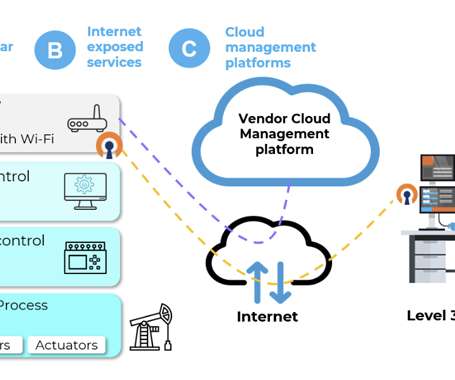
A set of 38 security vulnerabilities has been uncovered in wireless industrial internet of things (IIoT) devices from four different vendors that could pose a significant attack surface for threat actors looking to exploit operational technology (OT) environments.













































Let's personalize your content