TP-Link Router Botnet
Schneier on Security
MARCH 14, 2025
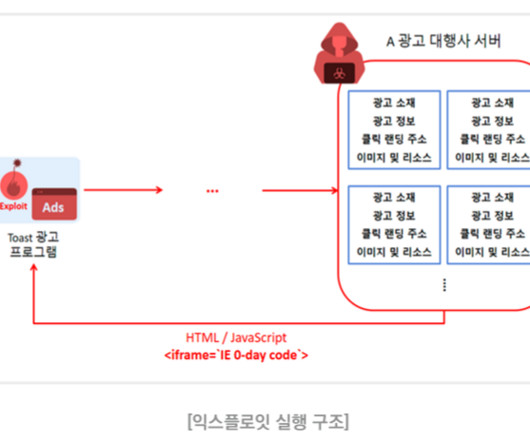
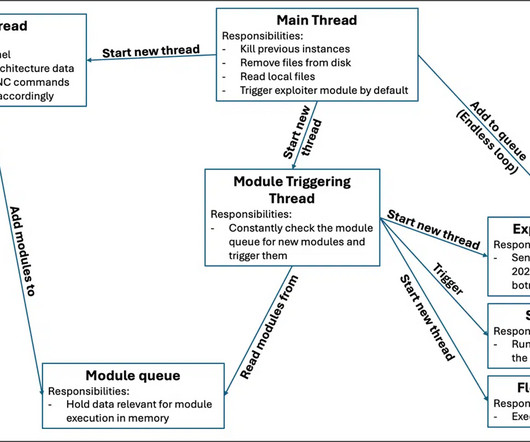
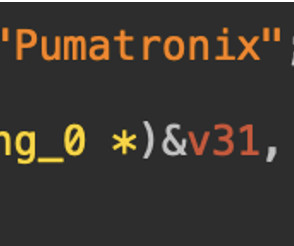
There is a new botnet that is infecting TP-Link routers: The botnet can lead to command injection which then makes remote code execution (RCE) possible so that the malware can spread itself across the internet automatically. Details.









































Let's personalize your content