Mollitiam Industries is the Newest Cyberweapons Arms Manufacturer
Schneier on Security
JUNE 23, 2021
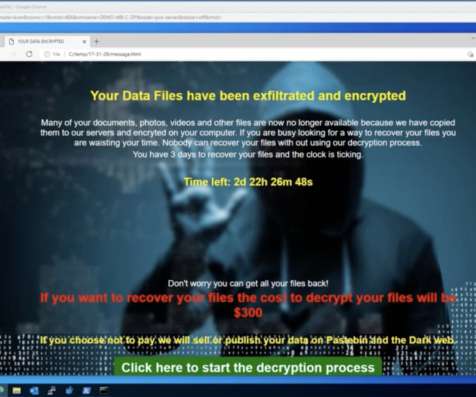
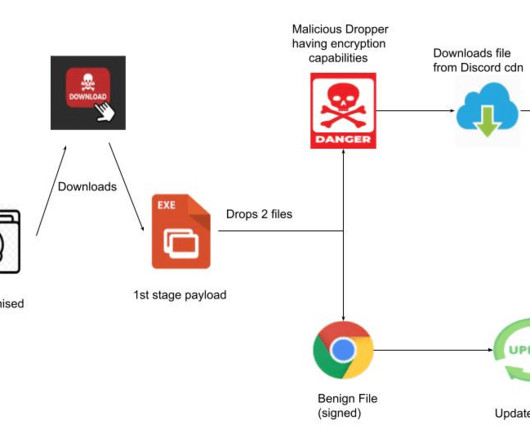
Its spyware is also said to be equipped with a keylogger, which means every keystroke made on an infected device — including passwords, search queries and messages sent via encrypted messaging apps — can be tracked and monitored.









































Let's personalize your content