Sophisticated Android spyware PhoneSpy infected thousands of Korean phones
Security Affairs
NOVEMBER 10, 2021
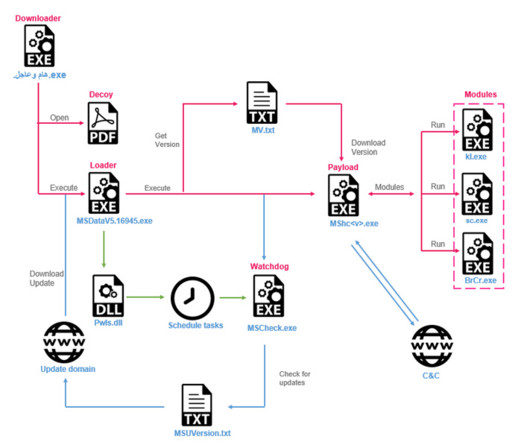
The malware already hit more than a thousand South Korean victims. Unlike other surveillance software that attempts to exploit vulnerabilities on the device, PhoneSpy disguised itself as a harmless application with purposes ranging from learning Yoga to watching TV and videos, or browsing photos. Zimperium concludes.























Let's personalize your content