SK Telecom revealed that malware breach began in 2022
Security Affairs
MAY 20, 2025
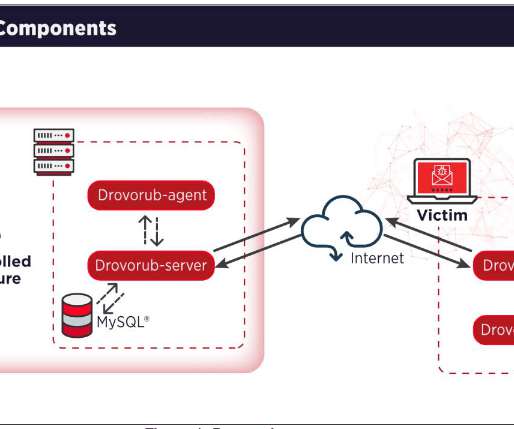
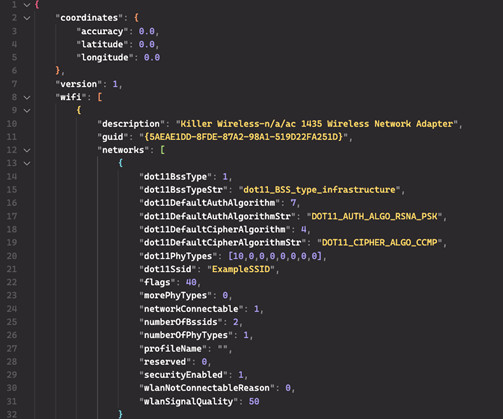
SK Telecom is South Koreas largest wireless telecom company, a major player in the countrys mobile and tech landscape. In April, SK Telecom reported that threat actors gained access to USIM-related information for customers following a malware attack. million users affected by a malware breach that exposed sensitive data. .













































Let's personalize your content