New PumaBot targets Linux IoT surveillance devices
Security Affairs
MAY 28, 2025
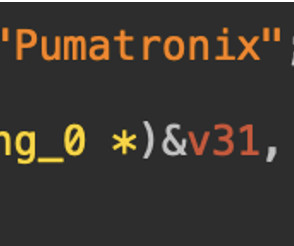
It checks the environment to avoid honeypots or restricted systems and looks specifically for the term Pumatronix, a maker of surveillance and traffic cameras, hinting at IoT targeting or an attempt to bypass certain devices. ” states the report.

















































Let's personalize your content