Experts detail a new Kimsuky social engineering campaign
Security Affairs
JUNE 8, 2023
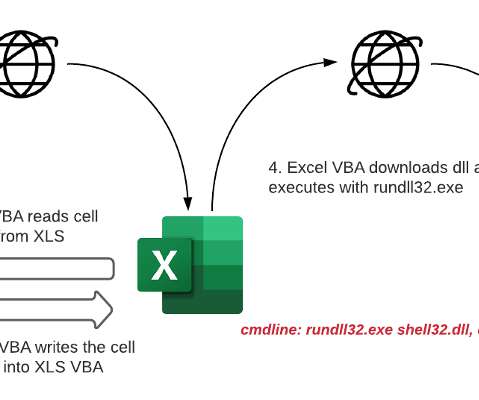
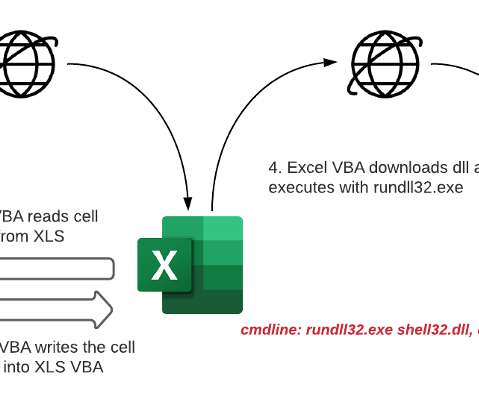
North Korea-linked APT Kimsuky has been linked to a social engineering campaign aimed at experts in North Korean affairs. SentinelLabs researchers uncovered a social engineering campaign by the North Korea-linked APT group Kimsuky that is targeting experts in North Korean affairs. ” concludes the report.













































Let's personalize your content