AI Dilemma: Emerging Tech as Cyber Risk Escalates
Trend Micro
JULY 2, 2025
Move faster than your adversaries with powerful purpose-built XDR, cyber risk exposure management, and zero trust capabilities Learn more Extend Your Team Extend Your Team.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Trend Micro
JULY 2, 2025
Move faster than your adversaries with powerful purpose-built XDR, cyber risk exposure management, and zero trust capabilities Learn more Extend Your Team Extend Your Team.

The Last Watchdog
JUNE 30, 2025
Yet, Browser AI Agents expose organizations to a massive security risk. Even if it is possible for users to add these guardrails, the overhead required to extensively write the security risk of every task performed by the agent in every prompt would probably outweigh the productivity gains. To register, users can click here.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Duo's Security Blog
JANUARY 14, 2025
In recent webinar Preventing Helpdesk Phishing with Duo and Traceless , Duo PMM Katherine Yang sat down with Gene Reich, Co-founder of Traceless to discuss why stronger identity verification is critical for MSPs and helpdesk teamsespecially with the increased accessibility of AI technologies driving identity fraud.

Security Boulevard
MARCH 21, 2025
Check out key findings and insights from the Tenable Cloud AI Risk Report 2025. 1 - Tenable: Orgs using AI in the cloud face thorny cyber risks Using AI tools in cloud environments? 1 - Tenable: Orgs using AI in the cloud face thorny cyber risks Using AI tools in cloud environments?

Security Boulevard
APRIL 18, 2025
Plus, learn why code-writing GenAI tools can put developers at risk of package-confusion attacks. Also, find out what Tenable webinar attendees said about identity security. Both frameworks have a Core section, which outlines detailed activities and outcomes aimed at helping organizations discuss risk management.

SecureList
MARCH 14, 2022
About the webinar. Currently, we assess that the risk of the cyber component of this conflict spilling over to Europe is medium-high. We advise organizations to: Take typical measures against DDoS attacks, ransomware and destructive malware, phishing, targeted attacks, supply-chain attacks and firmware attacks.

Cisco Security
NOVEMBER 2, 2022
“ Cisco Duo simplifies the passwordless journey for organizations that want to implement phishing-resistant authentication and adopt a zero trust security strategy. Password management is a challenging proposition for many enterprises, especially in light of BYOD and ever increasing sophistication of phishing schemes.
Security Boulevard
APRIL 4, 2025
document outlines these six key security control categories for mitigating AI systems' cyber risks. By implementing robust detection and mitigation strategies, organizations can significantly reduce their risk of compromise by fast flux-enabled threats, the document adds. The SANS Draft Critical AI Security Guidelines v1.1

Duo's Security Blog
APRIL 20, 2023
Through the first two months of 2023 alone, the Australian Competition and Consumer Commission’s Scamwatch reported more than 19,000 phishing reports with estimated financial losses of more than $5.2 What is phishing? This is part of what makes phishing attacks so dangerous.

Cisco Security
JULY 7, 2025
During his time with Cisco and at Robust Intelligence before that, Hyrum has been on a self-proclaimed crusade to get people to understand the cybersecurity risks from AI/ML. A PDF of the report can be downloaded directly from the National Academies, and a webinar that walks viewers through the report’s findings is also available.

Hacker's King
OCTOBER 26, 2024
Activities during this week include engaging workshops, informative webinars, and community events, all designed to empower individuals with the knowledge and skills necessary to navigate today’s cyber threats effectively. Promoting Cyber Hygiene Good cyber hygiene is about adopting habits that minimize security risks in everyday activities.
BH Consulting
JUNE 18, 2025
That was the message from a recent webinar that BH Consulting founder and CEO Brian Honan delivered for Géant, which provides networks and services to the research and education sector in Europe. Phishing has opened the door to smishing (phishing via SMS text message), vishing (video) and quishing (QR codes). You mean a scam.”

Duo's Security Blog
JULY 15, 2021
But on top of all of that, passwordless should also raise the bar by substantially reducing or even eliminating the risk of phishing attacks. That isn’t to say that every password-less solution needs to be phish-proof. Doing anything else would make push phishing attacks viable.

Duo's Security Blog
OCTOBER 18, 2021
Recently, while co-hosting a webinar that kicked off Cybersecurity Awareness Month, a panelist commented that cybersecurity and privacy are team sports on a campus, much like our athletic teams. The use of phishing to take over user accounts as a first step to gain access to a campus for a ransomware attack has been making the headlines.

Duo's Security Blog
OCTOBER 6, 2023
To achieve more resilience in this heightened risk environment, stepping up zero trust maturity is essential. In other words, it’s not just about implementing MFA to verify user trust, it’s about using phishing-resistant MFA with risk-based authentication , device posture checks and other security controls. And I get it.

Trend Micro
JUNE 26, 2025
Move faster than your adversaries with powerful purpose-built XDR, cyber risk exposure management, and zero trust capabilities Learn more Extend Your Team Extend Your Team.

The Hacker News
MARCH 19, 2025
Despite the many security tools and training programs available, identity-based attackslike phishing, adversary-in-the-middle, and MFA bypassremain a major challenge. Instead of accepting these risks and pouring resources into fixing problems after they occur, why not prevent attacks from happening in the first place? Our upcoming

Duo's Security Blog
OCTOBER 11, 2023
To learn more about how Duo’s access management trifecta empowers you to authenticate further and defend faster, be sure to tune into our webinar Authenticate Further, Defend Faster with Higher Security from Duo. Managing third-party risk is tricky, but not impossible. Talk about a team up! Talk about a team up!

Duo's Security Blog
DECEMBER 19, 2024
Phishing is still one of the most common attack vectors, and the holidays provide an especially appealing time to launch an attack thats been supercharged by modern natural language processing models and novel QR codes. No industry is spared this phishing season, though some are targeted more often than others.

Duo's Security Blog
SEPTEMBER 16, 2021
No Phishing, Please See the video at the blog post. To prevent phishing, your authentication solution should offer a few general properties. Passwordless should also raise the bar by substantially reducing or even eliminating the risk of phishing attacks. One Step at a Time See the video at the blog post.

Duo's Security Blog
NOVEMBER 20, 2023
Add to this, the risks of weak authentication factors such as SMS one-time passcodes and dormant or inactive accounts. On the proactive side, ITDR can detect policy misconfigurations, excessive privileges, and high-risk scenarios such as dormant or inactive accounts or accounts with MFA disabled.

Malwarebytes
APRIL 2, 2023
Apple fixes actively exploited vulnerability and introduces new features Steer clear of this EE phish that wants your card details 3 tips to raise your backup game 3 tips for creating backups your organization can rely on when ransomware strikes Stay safe!

Thales Cloud Protection & Licensing
FEBRUARY 19, 2025
Security Holes Weak Initial Authentication : Relying on less secure methods such as username/password combinations or SMS one-time passwords (OTPs) for FIDO authenticator registration exposes the system to phishing attacks, account takeovers, and fraudulent activities. PIN Length : The FIDO 2.0 Go beyond FIDO 2.1 Want to know more?

SecureWorld News
SEPTEMBER 29, 2020
Office supply phishing cyberattack campaign. A federal judge just sentenced a Nigerian national to three years in prison for being part of a phishing ring that effectively stole office supplies so it could resell them. It turns out, cybercriminals would like that person's login credentials because they have value.

Duo's Security Blog
APRIL 23, 2025
New threat types such as push-bombing, social engineering, and spear phishing are forcing organizations to do more than rely on MFA alone. Duo Risk-Based Authentication takes baseline authentication behavior and evaluates contextual signals to dynamically adjust authentication requirements in real time. Attacks have evolved.
Security Boulevard
MAY 2, 2025
Back in September 2024, CISA sounded the alarm on critical infrastructure organizations susceptibility to common, well-known attack methods in its CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments report. Coast Guard conducted in 2023. Enforce multi-factor authentication across all software development environments.

SecureWorld News
OCTOBER 19, 2021
TAG reported that Iranian-government-backed actors, known as APT35 and by the aliases Rocket Kitten and Charming Kitten, are quickly picking up speed, especially when it comes to implementing slick phishing attacks. Developing advanced phishing techniques to lure victims. Rocket Kitten successfully attacks university website.

Security Boulevard
FEBRUARY 14, 2022
How Enterprise Customer Identity Helps You Make Money, Slash Costs, and Reduce Risk. Here are four reasons why investing in great customer experiences with ForgeRock's enterprise CIAM will help your organization make money, slash costs, and reduce risk. Reduced Risk. ForgeRock also reduces risk with Zero Trust security.

SecureList
MAY 27, 2022
The group uses various malware families, including Wroba, and attack methods that include phishing, mining, smishing and DNS poisoning. You can find the recording of the webinar here and a summary/Q&A here. The phishing kit market. Typically, the smishing messages contain a very short description and a URL to a landing page.

Trend Micro
JUNE 10, 2025
Move faster than your adversaries with powerful purpose-built XDR, cyber risk exposure management, and zero trust capabilities Learn more Extend Your Team Extend Your Team.

Webroot
FEBRUARY 11, 2021
Impersonators are known to use phishing , Business Email Compromise (BEC) and domain spoofing to lure victims, and they’re always looking for new ways to innovate. This is why a multi-layered approach that can block phishing sites (including HTTPS) in real time, is key for staying safe. How Do Infiltrators Breach Systems?
Duo's Security Blog
JULY 6, 2023
The study also covered multi-factor authentication, identity protections, identity risks and identity vulnerabilities experienced. However, at the same time, we also enable our customers to implement the strongest multi-factor authentication (MFA) options available in the industry.
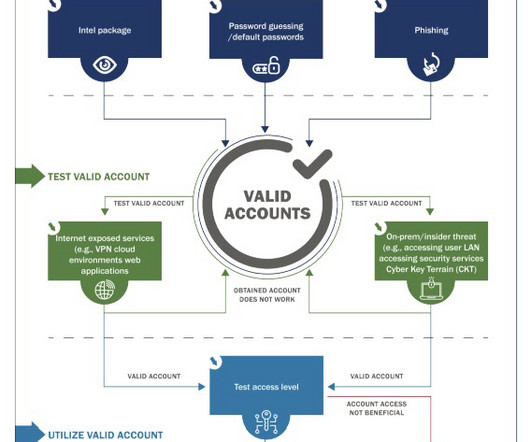
Security Boulevard
SEPTEMBER 20, 2024
That’s according to “ CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments, ” a report about the risk and vulnerability assessments (RVAs) conducted by the Cybersecurity and Infrastructure Security Agency (CISA) and the U.S. Dive into six things that are top of mind for the week ending September 20. Coast Guard (USCG).

CyberSecurity Insiders
APRIL 10, 2023
In the current digital landscape, identity security has gained paramount importance due to the growing cyber risks posed by phishing and social engineering attacks utilizing AI. Thus, a robust identity security framework is essential to safeguard against these risks and ensure the protection of personal information.

eSecurity Planet
MAY 28, 2024
Cloud security issues refer to the threats, risks, and challenges in the cloud environment. Risks include potential damage from cyber threats and vulnerabilities. Malware in Cloud Storage Buckets Malware threatens cloud storage buckets due to misconfigurations, infected data, and phishing.

Digital Shadows
AUGUST 17, 2021
What is Phish(ing)? But, never mind the dozens of other reports and white papers about phishing that come out every year from security industry leaders, let’s take a look at the 2021 Verizon DBIR. Why should I care about Phish? The reason why phishing is still reigning supreme?

Security Boulevard
MARCH 19, 2021
These detect phishing emails and remove threats from messages, documents and other files and disable any URLs before they even enter the network, a process known as content sanitization. Yet they are not without risk in terms of cybersecurity. This is where advanced email security solutions can play an important role. Request a Demo.

Security Affairs
OCTOBER 5, 2023
Other potential risks include targeted phishing attacks where criminals could send convincing phishing emails using insider information from the exposed database to target employees, clients, or vendors. He identifies real world examples of how exposed data can be a much bigger risk to personal privacy.

Duo's Security Blog
SEPTEMBER 1, 2023
Be sure to check out our upcoming webinar The State of Passkeys in the Enterprise on September 7th at 9am PST | 12pm EST. Passkeys and Cloud Sites Cloud sites are where the web applications are hosted. An alternate site cannot be substituted, mitigating the threat of phishing. Want to dig in deeper on the password vs. passkey debate?

Duo's Security Blog
FEBRUARY 6, 2024
Addressing identity-based attacks Duo has made a number of significant investments in identity security over the last several years with the release of Duo’s Trust Monitor, Duo’s Risk-Based Authentication, and moving Duo’s Trusted Endpoints feature into Duo’s Essentials edition. Stay tuned!

Security Boulevard
JULY 6, 2023
According to the 2023 ForgeRock Identity Breach Report , fraudsters are using generative AI to execute phishing emails, create malicious code, and deliver voice or video-based impersonation attacks, known as "deepfakes," that are becoming more frequent and more difficult for humans to detect.

Security Boulevard
MARCH 17, 2021
DLP policies are highly flexible and granular, and can easily extend to scanned documents and images, while the Clearswift DLP also protects data from phishing or ransomware attacks via its unique Structural Sanitization feature. Request a Demo. Additional Resources. Featured: .
Security Boulevard
MAY 30, 2025
In addition, discover what webinar attendees told Tenable about their cloud security challenges. Here's an overview of the five stages of an AI system and the 13 security principles that must be adopted: Secure design stage Raise awareness about AI security threats and risks. Evaluate the threats and manage the risks to the AI system.

Duo's Security Blog
NOVEMBER 6, 2023
Passwords that are easily detectable or reused often are vulnerable to phishing attacks. A smart user, when faced with the risk of stolen credentials, knows better than to face this threat alone. It’s also the foundation for a passwordless future, powering-up phishing resistance and user experience to defend against attackers.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content