Road Tolls Scams Rise on FBI's Radar; Public Warned Against Smishing
SecureWorld News
MARCH 18, 2025
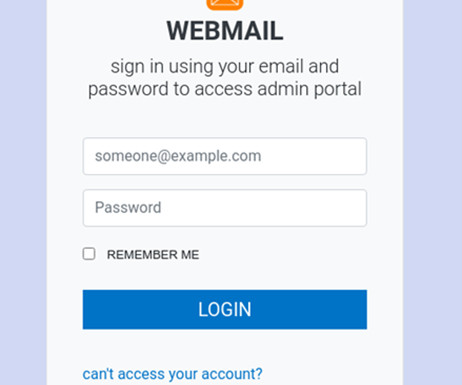
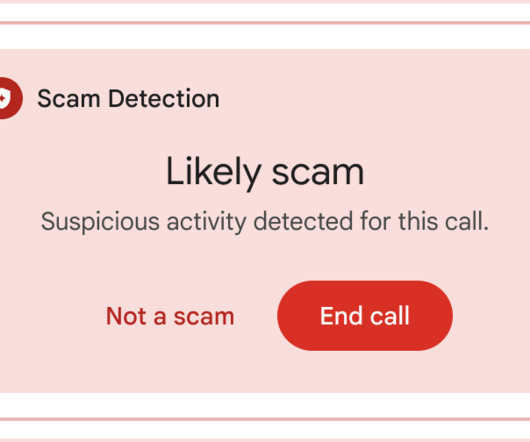
In recent months, a sophisticated scam has emerged, targeting drivers across the United States with fraudulent text messages about unpaid road tolls. Cybersecurity firm Palo Alto Networks reported that a threat actor has registered more than 10,000 domains to impersonate toll services and package delivery services in at least 10 U.S.


















































Let's personalize your content