GST Invoice Billing Inventory exposes sensitive data to threat actors
Security Affairs
DECEMBER 6, 2023
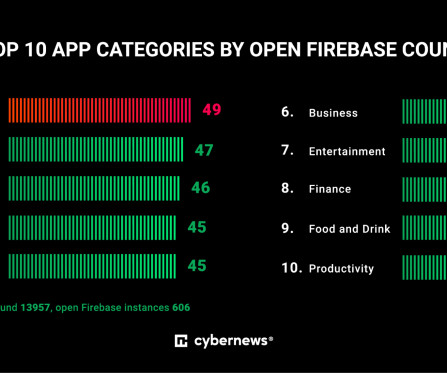
This means that threat actors can get their hands on API (application programming interface) keys, Google Storage buckets, and unprotected databases and exploit that information simply by analyzing publicly available information about apps. At the time of writing this article, the app had a 4-star (out of 5) rating based on 12K reviews.


















































Let's personalize your content