This Service Helps Malware Authors Fix Flaws in their Code
Krebs on Security
MAY 18, 2020
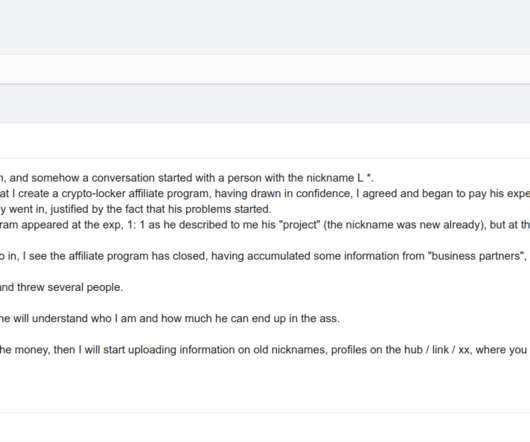
But the reality is most malicious software also has its share of security holes that open the door for security researchers or ne’er-do-wells to liberate or else seize control over already-hacked systems. biz , which frequently blogs about security weaknesses in popular malware tools. is cybercrime forum.
















































Let's personalize your content