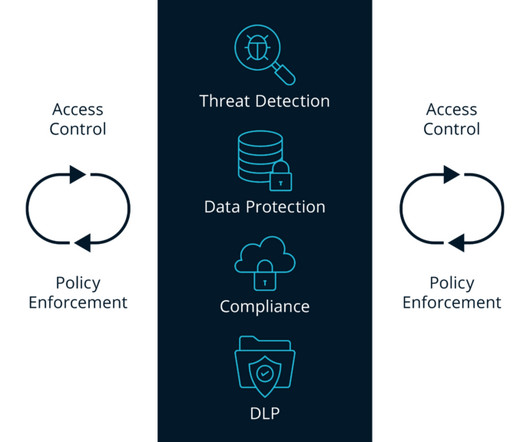
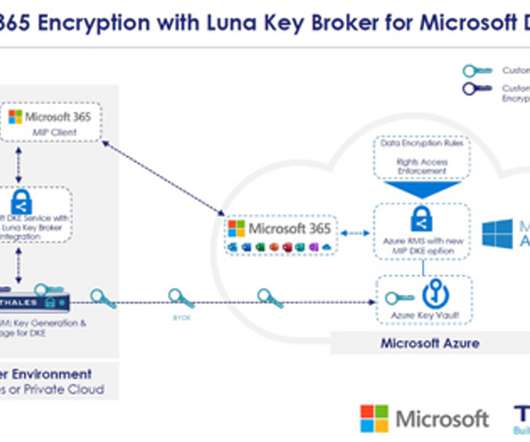
Four Advantages of a CASB
Security Boulevard
APRIL 11, 2023
The CASB, or Cloud Access Security Broker, was born out of necessity in response to the rapid increase in use of cloud-based services and SaaS applications. However, those solutions can’t be used when the data lives […] The post Four Advantages of a CASB first appeared on Banyan Security.









































Let's personalize your content