Building a Strong Business Case for Security and Compliance
The State of Security
MAY 10, 2022
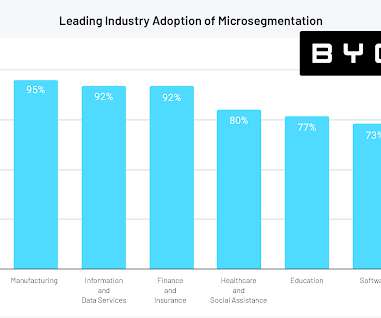
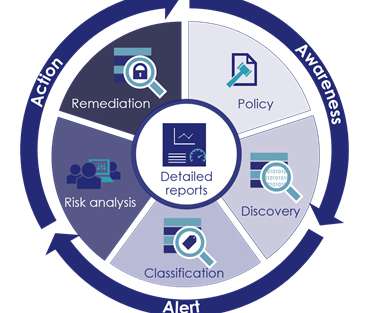
Compliance is a key part of any organisation and in business terms, it is about ensuring companies of all sizes and their employees comply with existing national and international laws. The post Building a Strong Business Case for Security and Compliance appeared first on The State of Security.













































Let's personalize your content