10 Database Security Best Practices You Should Know
The State of Security
FEBRUARY 24, 2021
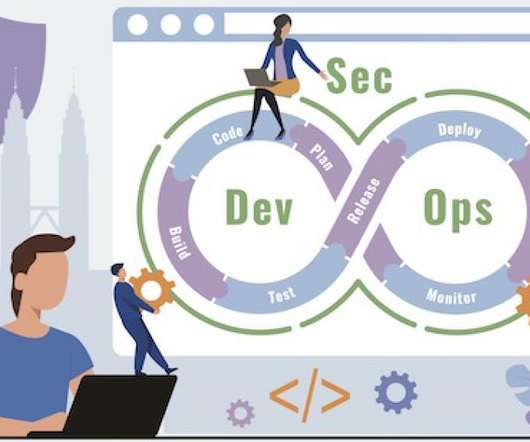
While this result is quite staggering, it also sends a clear message of the need for effective database security measures. Database security measures are a bit different from website security practices. The post 10 Database Security Best Practices You Should Know appeared first on The State of Security.















































Let's personalize your content