U.S. Internet Leaked Years of Internal, Customer Emails
Krebs on Security
FEBRUARY 14, 2024
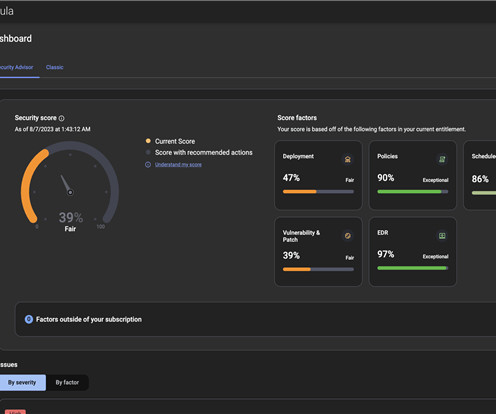
has a business unit called Securence , which specializes in providing filtered, secure email services to businesses, educational institutions and government agencies worldwide. Internet/Securence says your email is secure. Hold Security founder Alex Holden said his researchers had unearthed a public link to a U.S.











































Let's personalize your content