CISA adds Google Chromium V8 Type Confusion bug to its Known Exploited Vulnerabilities catalog
Security Affairs
FEBRUARY 7, 2024
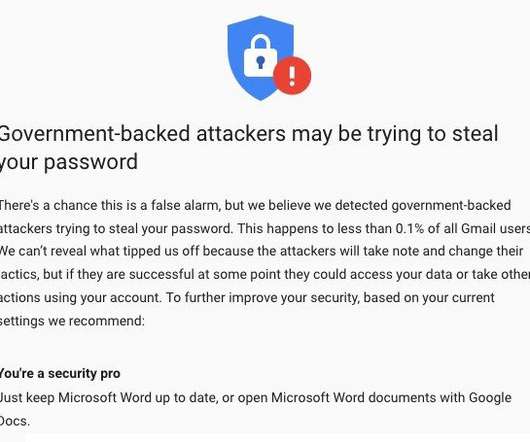
Cybersecurity and Infrastructure Security Agency (CISA) added a Google Chromium V8 Type Confusion bug, tracked as CVE-2023-4762 , to its Known Exploited Vulnerabilities (KEV) catalog. TAG observed these exploits delivered in two different ways: the MITM injection and via one-time links sent directly to the target.








































Let's personalize your content