TAG-70 Spying Campaign Targets Europe, Iran
Penetration Testing
FEBRUARY 17, 2024
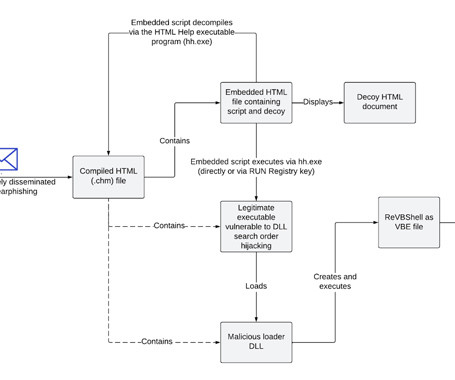
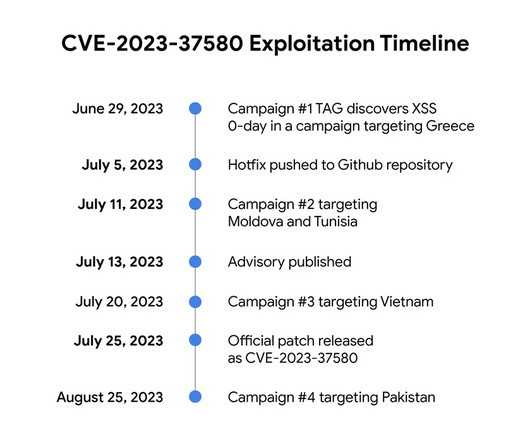
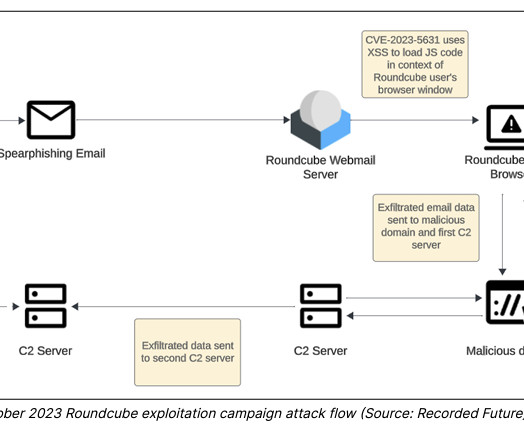
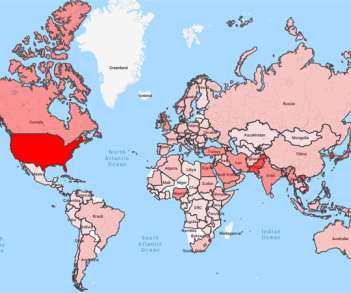
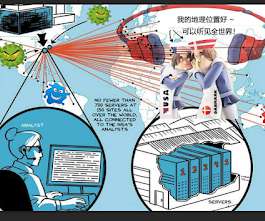
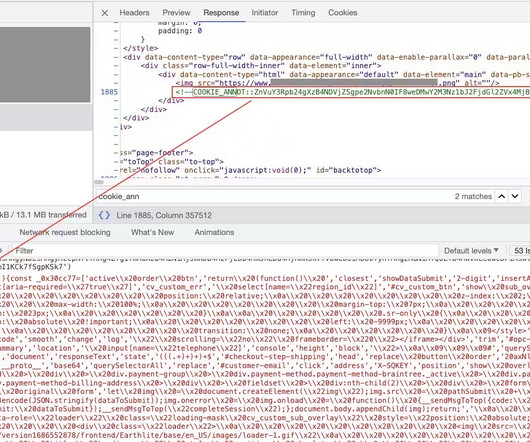
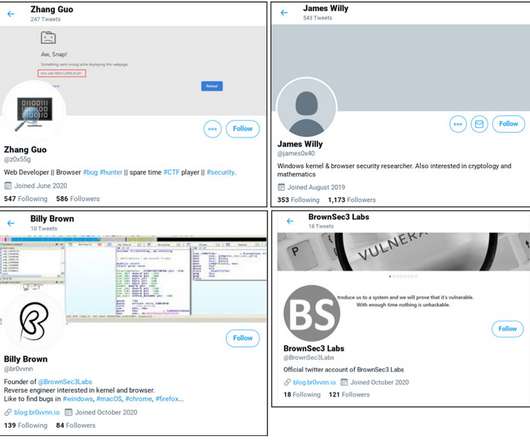
The ongoing war in Ukraine has intensified an already complex world of cyberwarfare, and groups like TAG-70 underscore the urgent need to counter state-sponsored espionage actors. Also operating under names like Winter Vivern, TA473,... The post TAG-70 Spying Campaign Targets Europe, Iran appeared first on Penetration Testing.















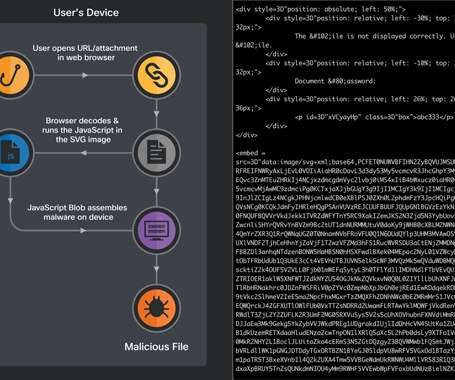
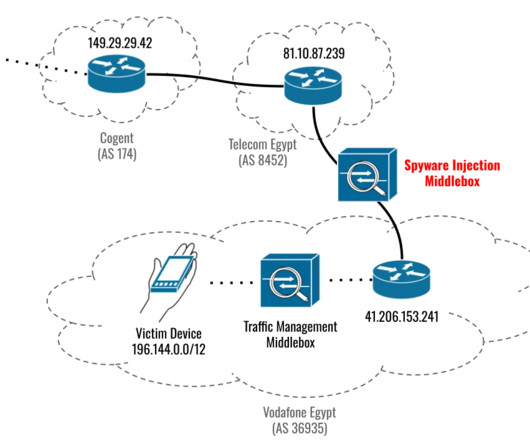










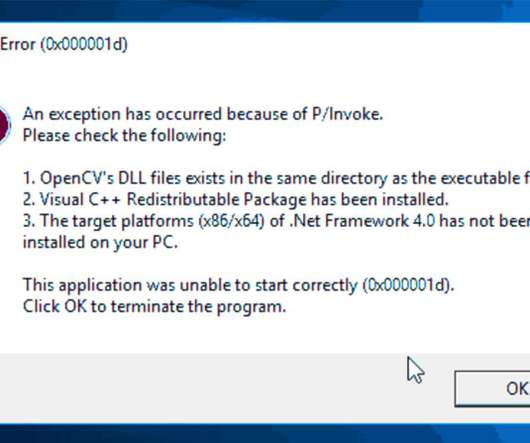
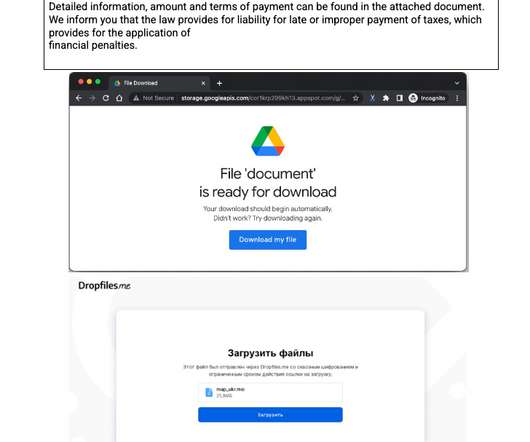











Let's personalize your content