Cyber Playbook: An Overview of PCI Compliance in 2022
Herjavec Group
MARCH 24, 2022
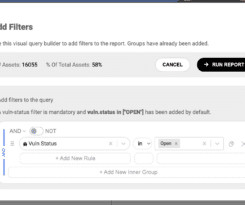
While PCI Compliance has certainly seen a mix of both new trends and legacy approaches, let’s take a look at the newest and most talked-about topics in 2022: Approved Scanning Vendor Lessons Learned. html tags, and links to 3rd party sources, end-user telemetry recording, etc. PCI Data Security Standards v4.0.














































Let's personalize your content