Email Security Flaw Found in the Wild
Schneier on Security
NOVEMBER 21, 2023
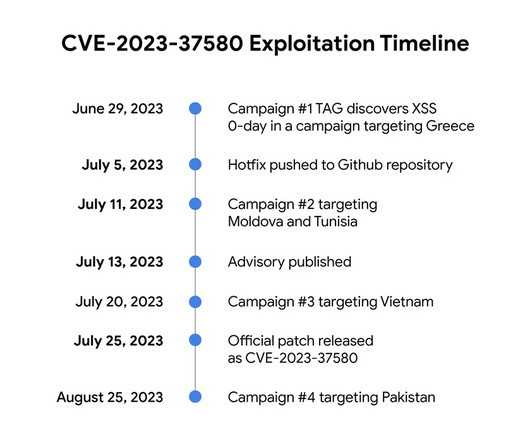
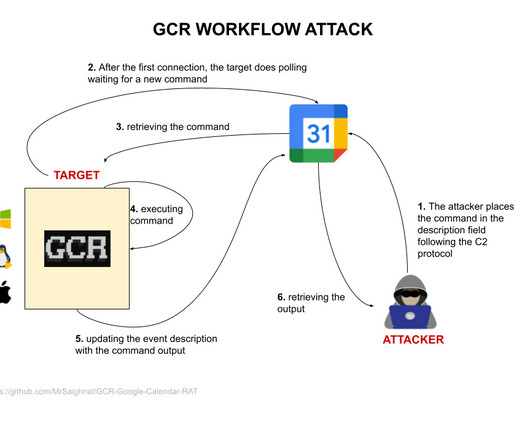
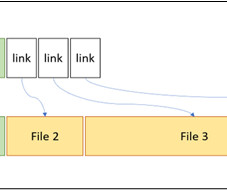
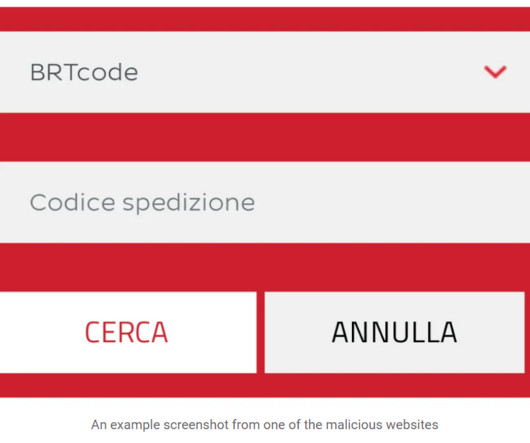
TAG has observed four different groups exploiting the same bug to steal email data, user credentials, and authentication tokens. Most of this activity occurred after the initial fix became public on Github.






































Let's personalize your content