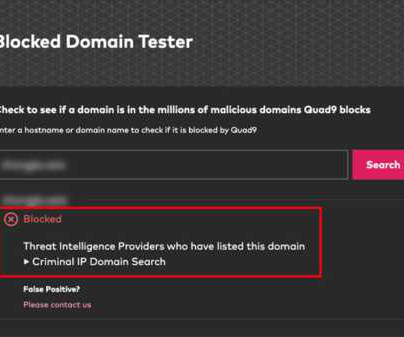
News alert: Criminal IP and Quad9 collaborate to exchange domain and IP threat intelligence
The Last Watchdog
MAY 13, 2024
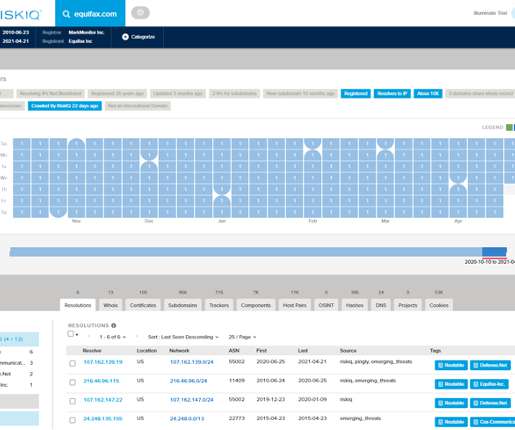
This global threat intelligence is updated daily and can be accessed through flexible API integration enabling seamless incorporation of the data into existing security systems, such as SOAR and SIEM. Users can check their own credit usage for specific features (Web, Vulnerability Scanner, Tags, etc.)






























Let's personalize your content