Social Engineering from the Attacker Perspective
Security Through Education
FEBRUARY 9, 2022
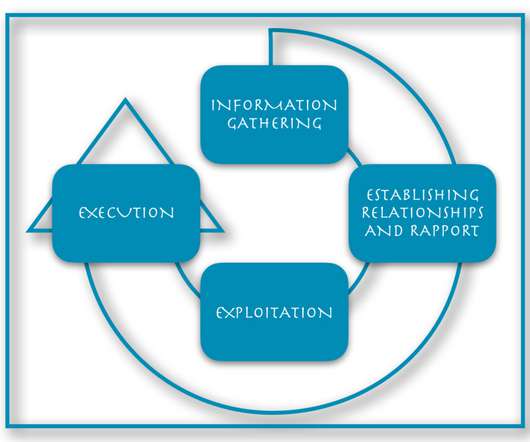
If you Google “social engineering,” you will get a very different and more negative definition. By understanding social engineering from the attacker perspective, you’ll be in a better position to protect yourself. Attacker Perspective. This same perspective is used in social engineering attacks.










































Let's personalize your content