Security Roundup April 2024
BH Consulting
APRIL 18, 2024
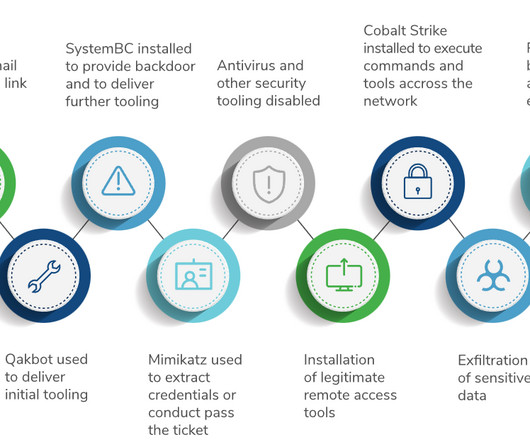
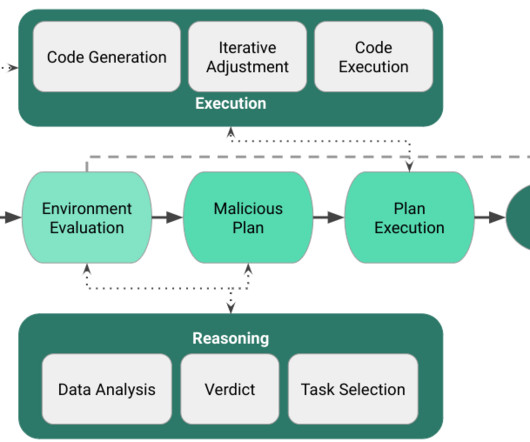
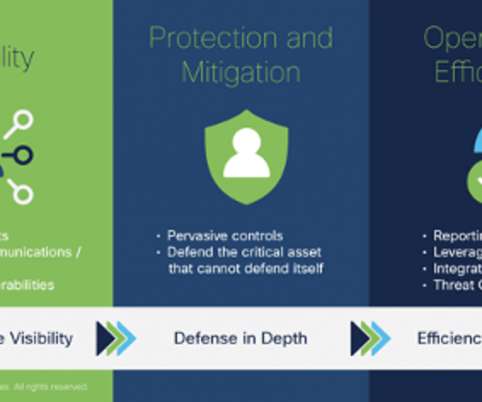
Curated advice, guidance, learning and trends in cybersecurity and privacy, as chosen by our consultants. Emerging security threats and trends Who doesn’t enjoy some future-gazing? Cybersecurity so often involves reacting to what’s happened, but it’s always worth keeping one eye on what’s coming next.

















































Let's personalize your content