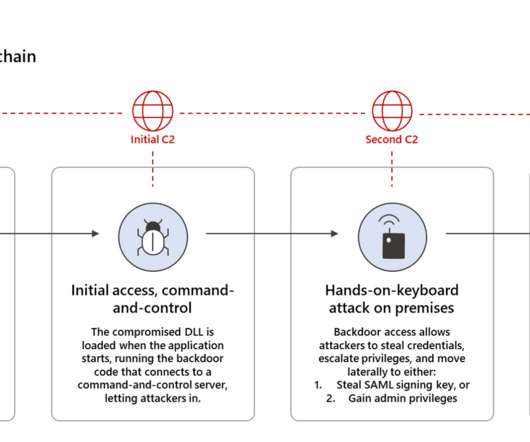
The malicious code in SolarWinds attack was the work of 1,000+ developers
Security Affairs
FEBRUARY 15, 2021
Microsoft says it found 1,000-plus developers’ fingerprints on the SolarWinds attack. Microsoft’s analysis of the SolarWinds supply chain attack revealed that the code used by the threat actors was the work of a thousand developers. And the answer we came to was, well, certainly more than 1,000.”

























Let's personalize your content