Tor Over VPN Guide: How To Combine Tor Browser With VPN [+5 Best VPNs]
SecureBlitz
MAY 24, 2022
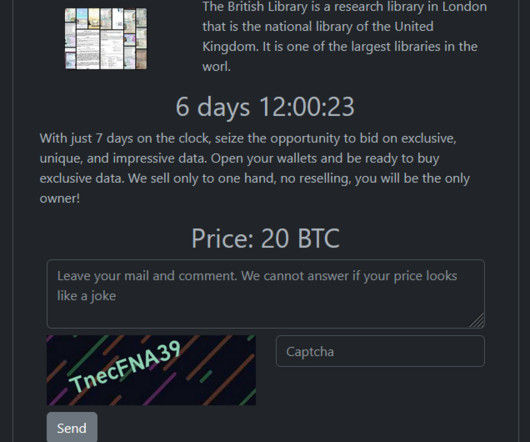
In this Tor over VPN Guide, we will show you how to combine the Tor Browser with VPN. The post Tor Over VPN Guide: How To Combine Tor Browser With VPN [+5 Best VPNs] appeared first on SecureBlitz Cybersecurity.









































Let's personalize your content