From Scanners to Strategies: How Attack Surface Management Enhances Vulnerability Scanning
NetSpi Executives
MARCH 19, 2024
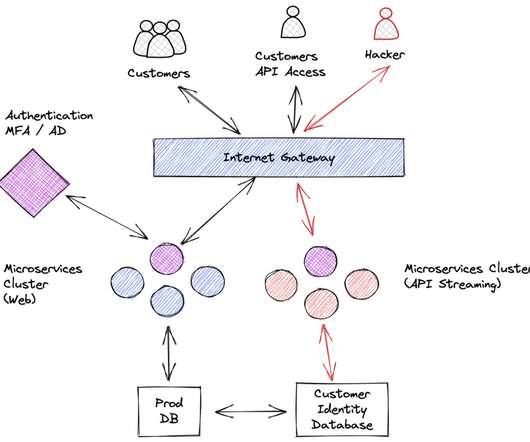
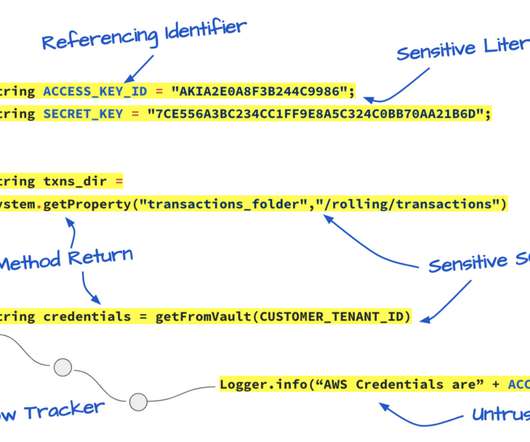
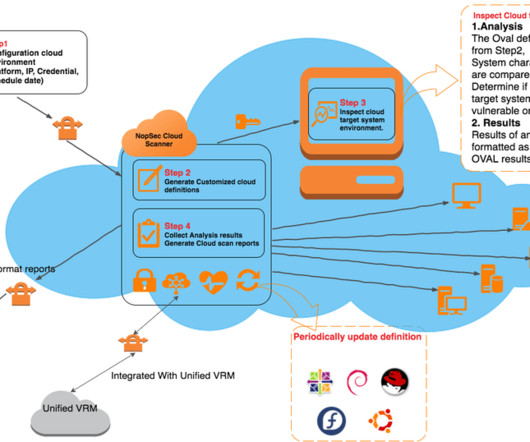
Vulnerability scanners help scan known assets, but what about the assets you don’t know exist? Why vulnerability scanners aren’t enough The issue lies in the fact that vulnerability scanners can only scan entities you tell them to. That’s where NetSPI ASM comes in.


























Let's personalize your content