Inside the Massive Naz.API Credential Stuffing List
Troy Hunt
JANUARY 17, 2024
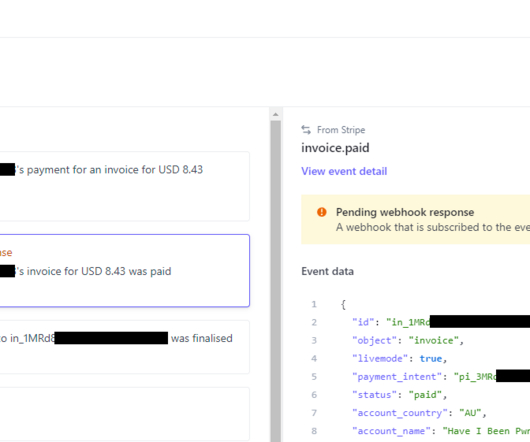
Here's what I found: 319 files totalling 104GB 70,840,771 unique email addresses 427,308 individual HIBP subscribers impacted 65.03% of addresses already in HIBP (based on a 1k random sample set) That last number was the real kicker; when a third of the email addresses have never been seen before, that's statistically significant.




































Let's personalize your content