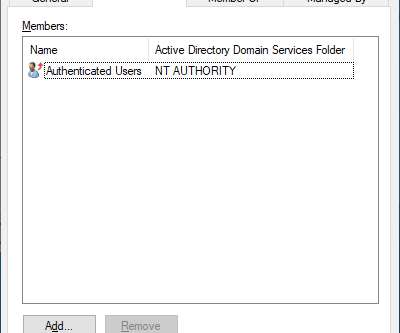
Understanding the Risks of Pre-Windows 2000 Compatibility Settings in Windows 2022
Security Boulevard
NOVEMBER 29, 2021
The post Understanding the Risks of Pre-Windows 2000 Compatibility Settings in Windows 2022 appeared first on Semperis. The post Understanding the Risks of Pre-Windows 2000 Compatibility Settings in Windows 2022 appeared first on Security Boulevard.














































Let's personalize your content