FBI Arrests Alleged Owner of Deer.io, a Top Broker of Stolen Accounts
Krebs on Security
MARCH 10, 2020
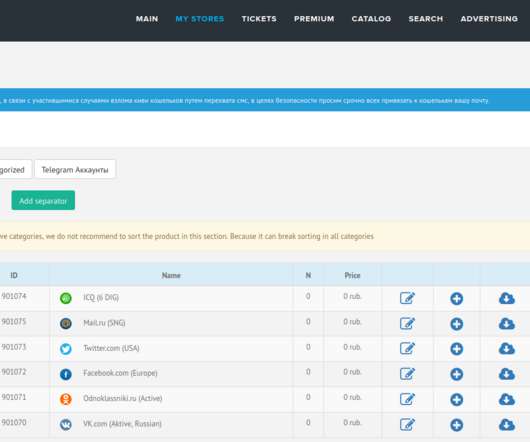
FBI officials last week arrested a Russian computer security researcher on suspicion of operating deer.io , a vast marketplace for buying and selling stolen account credentials for thousands of popular online services and stores. also is a favored marketplace for people involved in selling phony social media accounts.













































Let's personalize your content