Who’s Behind the ‘Web Listings’ Mail Scam?
Krebs on Security
MARCH 23, 2020
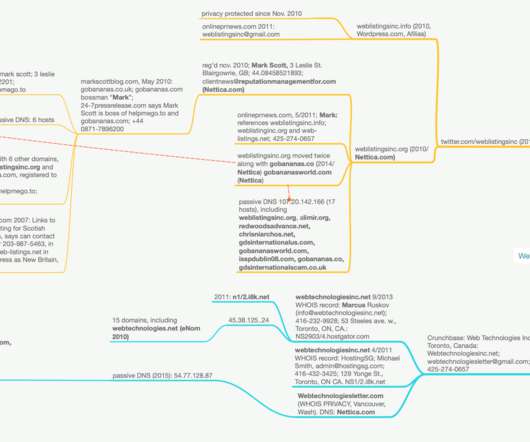
A Twitter account for Web Listings Inc. Searching the Internet for some of these Web listing domains mentioned in the company’s Twitter account brings up a series of press releases once issued on behalf of the company. Cached versions of this site from 2011 show it naming Web Listings Inc. as a business partner.
















































Let's personalize your content