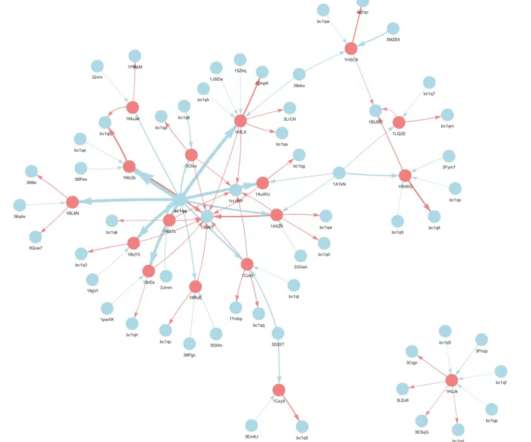
Glupteba botnet is back after Google disrupted it in December 2021
Security Affairs
DECEMBER 19, 2022
The blockchain-enabled botnet has been active since at least 2011, researchers estimated that the Glupteba botnet was composed of more than 1 million Windows PCs around the world as of December 2021. We also recommend monitoring DNS logs and keeping the antivirus software up to date to help prevent a potential Glupteba infection.”
















Let's personalize your content