Eavesdropping on SMS Messages inside Telco Networks
Schneier on Security
NOVEMBER 7, 2019
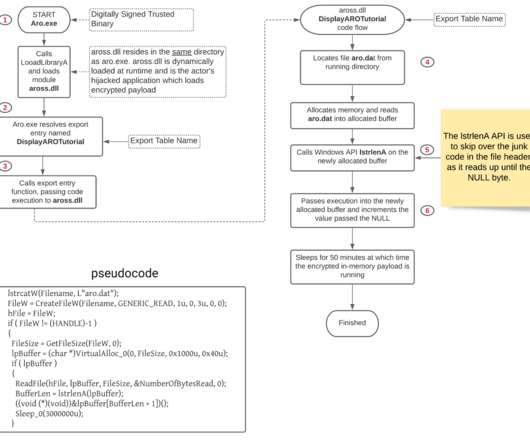
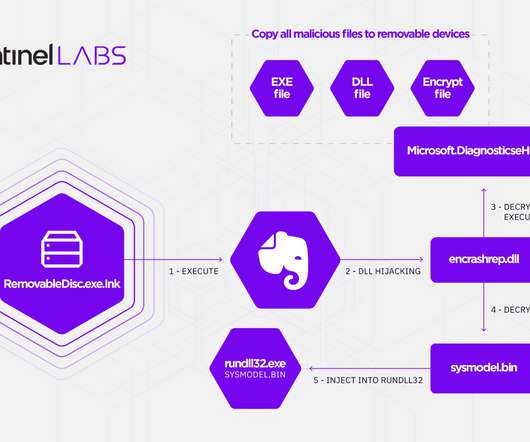
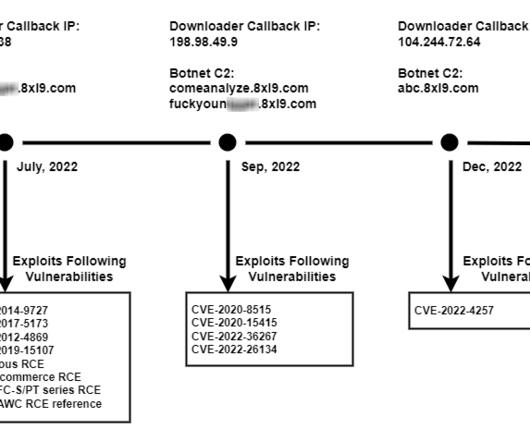
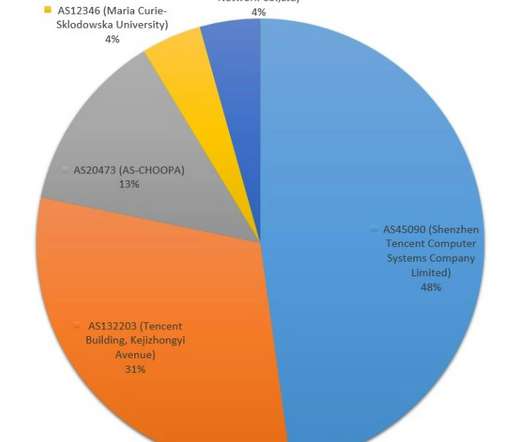
Fireeye reports on a Chinese-sponsored espionage effort to eavesdrop on text messages: FireEye Mandiant recently discovered a new malware family used by APT41 (a Chinese APT group) that is designed to monitor and save SMS traffic from specific phone numbers, IMSI numbers and keywords for subsequent theft.








































Let's personalize your content