Russians Hack FBI Comms System
Schneier on Security
SEPTEMBER 24, 2019
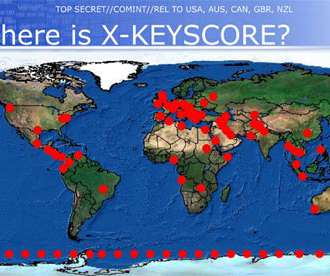
Yahoo News reported that the Russians have successfully targeted an FBI communications system: American officials discovered that the Russians had dramatically improved their ability to decrypt certain types of secure communications and had successfully tracked devices used by elite FBI surveillance teams. counterintelligence vulnerabilities.

























Let's personalize your content