We infiltrated an IRC botnet. Here’s what we found
Security Affairs
NOVEMBER 19, 2020
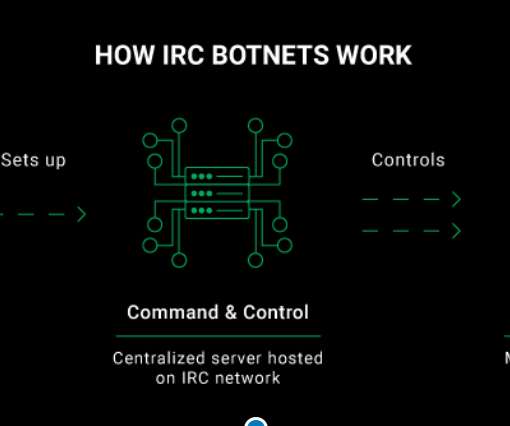
In order to capture malware and monitor cyberattacks across the internet in real-time, we run multiple honeypot systems that are contained in isolated execution environments, otherwise known as containers. They’re relatively easy to take down and there are far larger botnets powered by newer technologies such as the Internet of Things (IoT).




















Let's personalize your content