Hackers Exploit Zoom's Remote Control Feature in Cryptocurrency Heists
SecureWorld News
APRIL 22, 2025
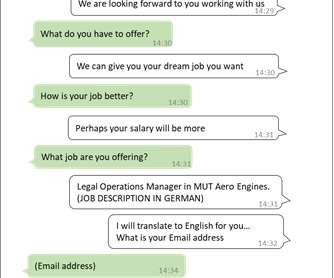
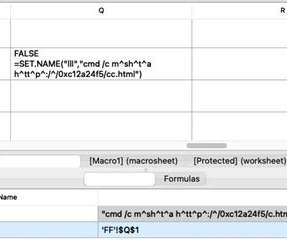
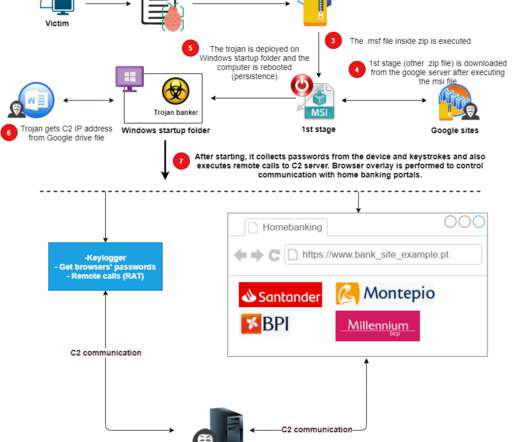
Once control is granted, the attacker can secretly install malware, including infostealers and remote access trojans (RATs), onto the victim's machine. The malware then exfiltrates sensitive data, including cryptocurrency wallet credentials, personal information, and private keys. billion hack of the Bybit exchange in February 2025.



































Let's personalize your content