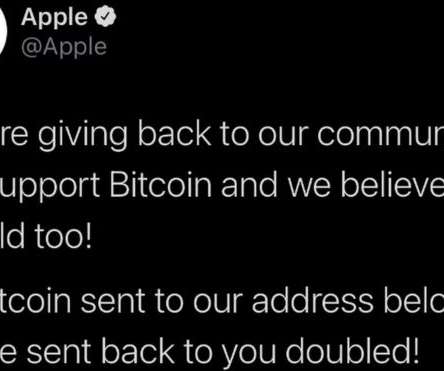
Several High-Profile Twitter accounts hacked in a Bitcoin scam
Security Affairs
JULY 16, 2020
The social media platform Twitter suffered one of the biggest cyberattacks in its history, multiple high-profile accounts were hacked. Twitter explained is was victim of a”coordinated social engineering attack” against its employees who gave attackers the access to its internal tools.







































Let's personalize your content