New EwDoor Botnet is targeting AT&T customers
Security Affairs
NOVEMBER 30, 2021
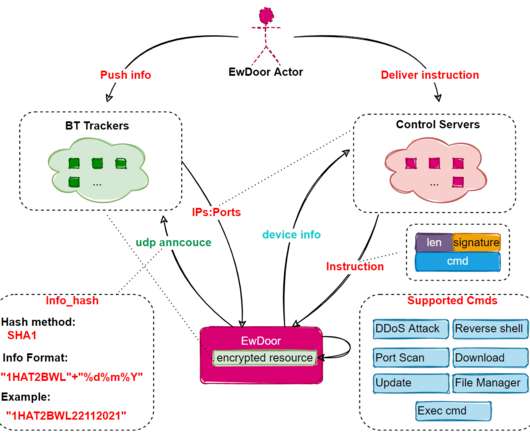
Experts from Qihoo 360’s Network Security Research Lab discovered a new botnet, dubbed EwDoor , that targets AT&T customers using EdgeMarc Enterprise Session Border Controller (ESBC) edge devices that are publicly exposed to the Internet. ” reads the analysis published by Qihoo 360.
















































Let's personalize your content