IoT, encryption, and AI lead top security trends for 2017
Tech Republic Security
APRIL 26, 2017
A new Forrester report identified the top 14 cybersecurity trends for enterprises to watch in 2017.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
APRIL 26, 2017
A new Forrester report identified the top 14 cybersecurity trends for enterprises to watch in 2017.

Security Affairs
JULY 29, 2019
According to experts at Sonicwall, scanning of random ports and the diffusion of encrypted malware are characterizing the threat landscape. Most of the attacks targeted non-standard ports and experts observed a spike in the number of encrypted malware. million encrypted malware attacks, +27% over the previous year. .”
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JUNE 6, 2017
At Infosecurity Europe 2017, High-Tech Bridge reported on the latest cybersecurity trends, touching on mobile and IoT security, DevSecOps, Bug Bounties, OWASP Top Ten and encryption.
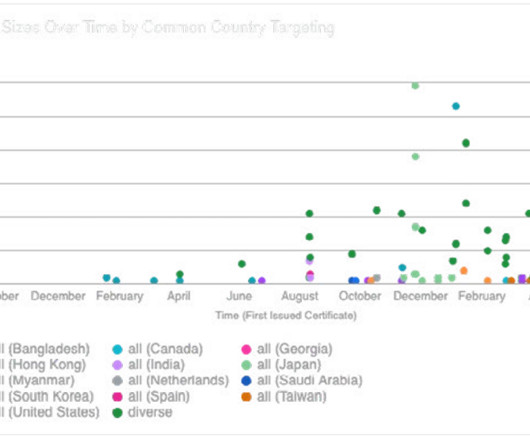
Security Affairs
JUNE 28, 2025
The malware’s core payload is encrypted in two layers with different decryption keys. SecurityScorecard researchers found that many devices in the LapDogs network are vulnerable to known flaws like CVE-2015-1548 and CVE-2017-17663 , linked to outdated mini_httpd servers. Most infected devices run lightweight web servers (e.g.,

Security Affairs
SEPTEMBER 29, 2018
Avast spotted a new IoT botnet, tracked as Torii, that appears much more sophisticated and stealth of the numerous Mirai variants previously analyzed. Security researchers spotted a new IoT botnet, tracked as Torii, that appears much more sophisticated and stealth of the numerous Mirai variants previously analyzed. Pierluigi Paganini.

eSecurity Planet
DECEMBER 7, 2023
Encryption uses mathematical algorithms to transform and encode data so that only authorized parties can access it. What Encryption Is and How It Relates to Cryptology The science of cryptography studies codes, how to create them, and how to solve them. How Does Encryption Process Data? How Does Encryption Process Data?

The Last Watchdog
MARCH 13, 2019
The drivers of IoT-centric commerce appear to be unstoppable. Count on the wide deployment of IoT systems to continue at an accelerated rate. There are already more IoT devices than human beings on the planet, according to tech industry research firm Gartner. Here’s what to expect: Evermore plugged in.
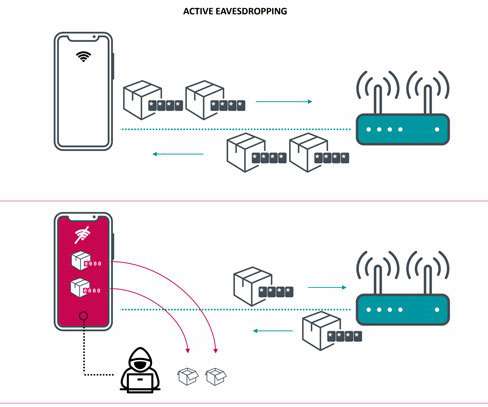
Security Affairs
FEBRUARY 26, 2020
The vulnerability could have a severe impact on the IT sector, the flawed chips are used in over a billion devices, including routers, smartphones, tablets, laptops, and IoT gadgets. This serious flaw, assigned CVE-2019-15126, causes vulnerable devices to use an all-zero encryption key to encrypt part of the user’s communication.”
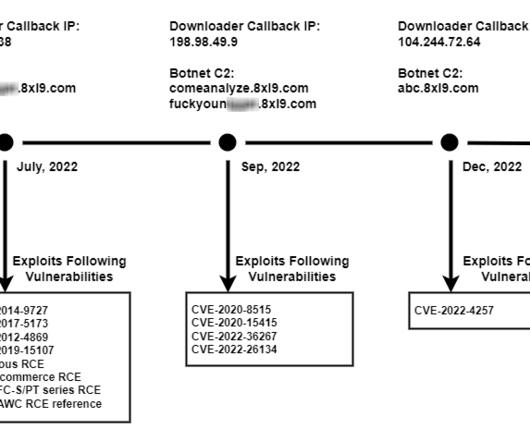
Security Affairs
FEBRUARY 16, 2023
During the second half of 2022, a variant of the Mirai bot, tracked as V3G4, targeted IoT devices by exploiting tens of flaws. Palo Alto Networks Unit 42 researchers reported that a Mirai variant called V3G4 was attempting to exploit several flaws to infect IoT devices from July to December 2022.

Thales Cloud Protection & Licensing
MARCH 10, 2021
What’s driving the security of IoT? In 2017, Tesla sent an over-the-air update to their Model S and X vehicles to extend maximum battery capacity and driving range, which allowed owners to drive an extra 30 miles outside the evacuation area as Hurricane Irma was bearing down on Florida. Guest Blog: TalkingTrust.
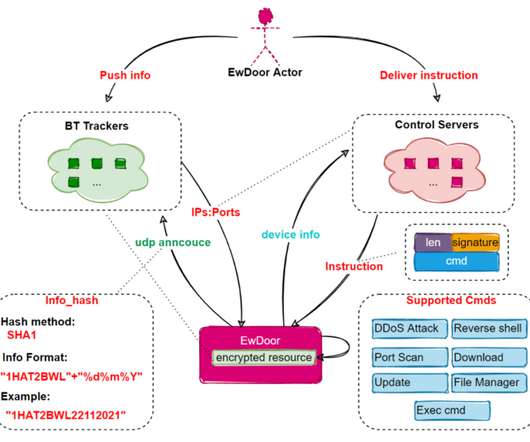
eSecurity Planet
DECEMBER 3, 2021
The botnet was able to exploit an older vulnerability in unpatched EdgeMarc Enterprise Session Border Controllers (ESBCs) that is tracked as CVE-2017-6079. It also uses TLS encryption to block attempts to intercept the network traffic and analysis of the malware, the researchers wrote.

Security Affairs
SEPTEMBER 10, 2018
Security experts with Unit 42 at Palo Alto Networks have discovered new variants of the Mirai and Gafgyt IoT malware targeting enterprises. Both botnets appear very interesting for two main reasons: The new Mirai variant targets the same Apache Struts vulnerability exploited in the 2017 Equifax data breach. Pierluigi Paganini.

The Last Watchdog
FEBRUARY 21, 2020
Related: Why PKI is well-suited to secure the Internet of Things PKI is the authentication and encryption framework on which the Internet is built. In the classic case of a human user clicking to a website, CAs, like DigiCert, verify the authenticity of the website and encrypt the data at both ends.

Security Affairs
FEBRUARY 2, 2024
” In July 2022, Schulte was found guilty in a New York federal court of stealing the agency’s hacking tools and leaking them to WikiLeaks in 2017. The hacking tools developed by the US cyber spies can target mobile devices, desktop computers, and IoT devices such as routers and smart TVs.
Security Affairs
NOVEMBER 11, 2020
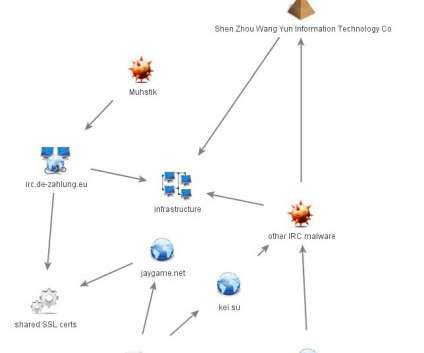
Muhstik botnet leverages known web application exploits to compromise IoT devices, now it targeting Oracle WebLogic, Drupal. Muhstik is a botnet that is known to use web application exploits to compromise IoT devices, it has been around for at least 2018. In the first stage of the attack, a payload downloads the other components. .

Security Affairs
APRIL 10, 2019
Mirai malware first appeared in the wild in 2016 when the expert MalwareMustDie discovered it in massive attacks aimed at Internet of Things (IoT) devices. which allows it to attack a wider range of Internet of Things (IoT) devices, Since the code of the Mirai botnet was leaked online many variants emerged in the threat landscape.
Security Affairs
JULY 23, 2020
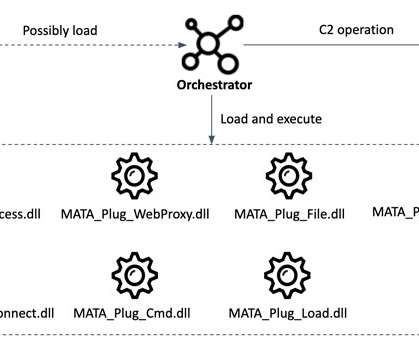
The Windows version of MATA is composed of a loader used to load an encrypted next-stage payload and the orchestrator module (“lsass.exe”). MATA is also able to target Linux-based diskless network devices, including such as routers, firewalls, or IoT devices.

Webroot
MARCH 15, 2021
Drafted by the Internet Engineering Task Force (ITEF) in 1998, it became an Internet Standard in 2017. On the other hand, IPv6 is based on 128-bit encryption. This is especially true for IoT devices. As internet-connected nodes in the form of IoT devices continue to proliferate, millions of new IPs will be needed.

Thales Cloud Protection & Licensing
DECEMBER 19, 2017
As 2017 draws to a close, the trends and innovations that will shape the technology industry over the coming weeks, months and years were brought into sharper focus over the course of the last twelve months. Collective appetite for this enterprization will definitely be a hot topic on the digital transformation agenda.

Thales Cloud Protection & Licensing
OCTOBER 27, 2017
One of the things we see every day at Thales is how the pace of change in organizations is pushing them to adapt and utilize cloud, big data, IoT and container technologies. Here’s what some analysts say about the topic: “66 percent of enterprises end up with more than one provider” – Carl Brooks, 451 Research, May 2017. “75

eSecurity Planet
JULY 28, 2021
For modern networks, the introduction of new endpoints – be it remote laptops for personnel or client IoT devices – is a roadblock being actively addressed. Since the 1970s, Public Key Infrastructure (PKI) has offered encryption , authentication, bootstrapping, and digital signatures to secure digital communications. Block Armour.

Security Affairs
AUGUST 2, 2020
The first campaign likely began in early 2014 and continued until mid-2017, while the second started in late 2018 and was still active in late 2019. These are encrypted with the actor’s public key and sent to their infrastructure over HTTPS. CISA and NCSC have identified two campaigns of activity for QSnatch malware.

Thales Cloud Protection & Licensing
MARCH 5, 2018
92% are leveraging IoT devices, which may include internet-connected heart-rate monitors, implantable defibrillators and insulin pumps. Control of data user access and encryption key management to make sure only those authorized to do so can access encrypted data as clear text. Almost all (96%) of U.S. Nearly half (48%) of U.S.

SecureList
DECEMBER 1, 2023
Most prolific groups This section looks at ransomware groups that engage in so-called “double extortion”, that is, stealing and encrypting confidential data. IoT attacks IoT threat statistics In Q3 2023, the distribution of devices attacking Kaspersky traps using the Telnet and SSH protocols did not change significantly.

Security Affairs
JULY 28, 2020
These are encrypted with the actor’s public key and sent to their infrastructure over HTTPS. The first campaign likely began in early 2014 and continued until mid-2017, while the second started in late 2018 and was still active in late 2019. Webshell functionality for remote access.

eSecurity Planet
APRIL 19, 2023
Since then Portnox continued to add capabilities, launched the first cloud-native NAC in 2017, and now offers a NAC SaaS solution, Portnox Cloud. For example, encryption keys, administrator passwords, and other critical information are stored in the Azure Key Vault in FIPS 140-2 Level 2-validated hardware security modules (HSMs).

CyberSecurity Insiders
JUNE 20, 2022
Cybersecurity researchers have found that the QNAP devices operating on weak passwords or operating outdated software are being targeted with the two said file-encrypting malware variants. First is the gang that is distributing DeadBolt Ransomware, and the second is the malware variant dubbed QNAPCrypt.

Security Affairs
JULY 23, 2018
Security experts are warning of an intensification of attacks powered by two notorious IoT botnets, Mirai and Gafgyt. The campaign leverages two different encryption schemes, the bot propagates only via exploits and prevents further infection of compromised devices through dropping packets received on certain ports using iptables.

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Satori DataSecOps 2021 Private BluBracket Software supply chain 2021 Private Cape Privacy Data security 2021 Private ZecOps Digital forensics 2019 Private SecurityScorecard Risk ratings 2017 Private Carbon Black Security software 2015 Acquired: VMware AVG Antivirus software 2015 Acquired: Avast. ForgePoint Capital.

eSecurity Planet
MAY 19, 2022
The vendor’s Secure SD-WAN product sits under Barracuda’s Network Protection solutions alongside zero trust access, industrial security for OT and IoT networks , and SASE. Networking and IT giant Cisco is an undisputed leader in the secure SD-WAN solution space. Features: Cisco SD-WAN. Open Systems.

Security Affairs
SEPTEMBER 1, 2023
EternalBlue is a Windows exploit created by the US National Security Agency (NSA) and used in the 2017 WannaCry ransomware attack. Imagine a large organization with a network infrastructure comprising multiple interconnected systems, including servers, workstations, and IoT devices. What is the EternalBlue vulnerability?

Thales Cloud Protection & Licensing
OCTOBER 9, 2018
Enter data-centric security… a set of technologies that lower the value of data through encryption, tokenization, data masking and access control methods. Further driving the adoption of big data technologies are applications like analytics, AI, machine learning and IoT which are all fueling the creation and growth of new data lakes.

eSecurity Planet
AUGUST 14, 2023
August 12 , 2023 Ford Auto’s TI Wi-Fi Vulnerability The Internet of Things (IoT) continues to expand and become a threat to connected businesses. 2017 Zyxel Vulnerability Under Active Attack Fortinet issued an alert about thousands of daily attacks looking to perform a command injection attack on end-of-life Zyxel routers.

Veracode Security
NOVEMBER 16, 2020
In 2017, we started a blog series talking about how to securely implement a crypto-system in java. Encryption/Decryption. There are some exciting advances in Java Cryptography since version 8, and also in the cryptographic community at large since we last spoke about this in Encryption/Decryption. Symmetric Encryption.
Security Affairs
DECEMBER 17, 2019
TP-Link addressed a critical zero-day vulnerability ( CVE-2017-7405 ) in its TP-Link Archer routers that could be exploited by attackers to remotely take their control over LAN via a Telnet connection without authentication. “This is a zero-day flaw that was not previously reported and can affect both home and business environments.”

IT Security Guru
JUNE 17, 2024
Data Breach and Privacy Concerns Most ransomware attacks often involve data theft before encrypting the victim’s data. Further examples like the Maersk NotPetya and UK NHS WannaCry incidents (both taking place in 2017) still being popular examples show the impact on an organisation’s reputation over time.

eSecurity Planet
FEBRUARY 16, 2021
All of your files are encrypted with RSA-2048 and AES-128 ciphers.” ” Or you might see a readme.txt stating, “Your files have been replaced by these encrypted containers and aren’t accessible; you will lose your files on [enter date] unless you pay $2500 in Bitcoin.” IMPORTANT INFORMATION !!!

SecureList
MAY 31, 2021
If the victim organization is slow to pay up, even though its files are encrypted and some of its confidential data has been stolen, the attackers additionally threaten to carry out a DDoS attack. IoT attacks. IoT threat statistics. New additions to the ransomware arsenal. Trojan-Downloader.Shell.Agent.p.

eSecurity Planet
JULY 8, 2024
These vulnerabilities affected diverse areas, including network infrastructure, software libraries, IoT devices, and even CPUs. Traeger addressed unauthorized controls on IoT grills before July 4th. Cisco discovered a command injection issue, while a side-channel attack exposed Intel CPUs. Rockwell Automation handled RCE issues.
Krebs on Security
JUNE 25, 2020
Justice Department today criminally charged a Canadian and a Northern Ireland man for allegedly conspiring to build botnets that enslaved hundreds of thousands of routers and other Internet of Things (IoT) devices for use in large-scale distributed denial-of-service (DDoS) attacks. ” Shwydiuk, a.k.a. — pleaded guilty in Sept.

Spinone
DECEMBER 20, 2019
Ransomware was proliferated in 2016 and 2017 and then seemed to be on the decline. However, the company suggests cybercriminals will target less common and more vulnerable victims, such as individuals with high net values and connected devices (IoT). November 2, 2019 – Government of Nunavut operations affected by ransomware.

eSecurity Planet
OCTOBER 5, 2021
A token acts as an electronic cryptographic key that unlocks the device or application, usually with an encrypted password or biometric data. Two-factor authentication is also being deployed for mobile security and by Internet of Things companies such as Nest to secure IoT devices. Rise of multi-factor authentication.

SC Magazine
JUNE 23, 2021
A 2017 agency letter to participating entities encouraged cybersecurity as part of development plans but did not require it. These entities commonly focus on passwords, encryption, and access monitoring. But again, it’s not specific to medical devices.

eSecurity Planet
FEBRUARY 3, 2021
Read Also: The IoT Cybersecurity Act of 2020: Implications for Devices. In 2017, CyberArk published findings on a new attack vector related to certificate signing. The build process is on trial, from vulnerabilities in the supply chain for IoT devices to the Solorigate breach. Encryption. The Rise of Golden SAML Attacks.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content