Hackers Exploit Zoom's Remote Control Feature in Cryptocurrency Heists
SecureWorld News
APRIL 22, 2025
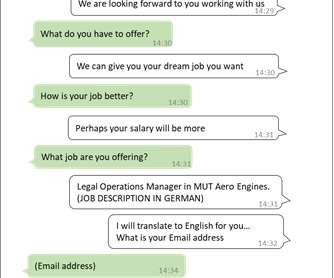
Victims are sent unsolicited invitations to join Zoom calls, often via links in phishing emails or messages. According to Security Alliance's findings, the campaign relied on social engineering and Zoom's remote control feature to infect targets with malware. billion hack of the Bybit exchange in February 2025.












































Let's personalize your content