Critical Zyxel Firewall Vulnerability Exploited in DDOS Attacks
Heimadal Security
JULY 21, 2023
Multiple DDoS botnets have actively exploited a critical vulnerability discovered in Zyxel firewall models, as revealed by cybersecurity researchers.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Heimadal Security
JULY 21, 2023
Multiple DDoS botnets have actively exploited a critical vulnerability discovered in Zyxel firewall models, as revealed by cybersecurity researchers.

The Last Watchdog
APRIL 30, 2025
The new Link11 WAAP (Web Application and API Protection) SaaS platform combines comprehensive DDoS protection against web attacks with ML-based adaptive security and API protection. At the end of 2023, Link11 secured an investment of 26.5 Link11 is a BSI-qualified provider of DDoS protection for critical infrastructure.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
MAY 1, 2024
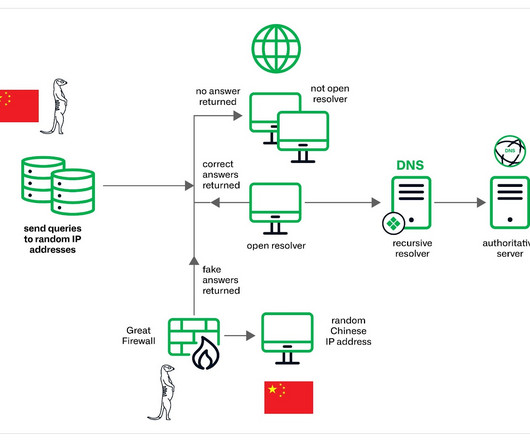
The experts noticed a spike in activity observed in September 2023. The threat actors appear to have the capability to control China’s Great Firewall and were observed utilizing a novel technique involving fake DNS MX records. However, low-volume attacks resembling Slow Drip DDoS attacks have persisted since then.

eSecurity Planet
JANUARY 14, 2022
Distributed denial of service (DDoS) attacks can cripple an organization, a network, or even an entire country, and they show no sign of slowing down. DDoS attacks may only make up a small percentage of security threats, but their consequences can be devastating. According to Imperva Research Labs, DDoS attacks tend to come in waves.

SecureList
SEPTEMBER 21, 2023
We conducted an analysis of the IoT threat landscape for 2023, as well as the products and services offered on the dark web related to hacking connected devices. In the first half of 2023, 97.91% of password brute-force attempts registered by our honeypots targeted Telnet, and only 2.09%, SSH. Our advantages: 1.

SecureWorld News
JUNE 9, 2025
Global data reveals that cyberattacks rose by 131% between 2022 and 2023 across the aviation industry, with a 74 percent increase since 2020, underscoring the profundity of this threat. In the first half of 2023 alone, aviation cyberattacks surged by 24% worldwide, fueling disruptions from flight-planning systems to passenger services.
Security Affairs
JANUARY 29, 2025
A new variant of the Mirai-based botnet Aquabot targets vulnerable Mitel SIP phones to recruit them into a DDoS botnet. Aquabot is a Mirai-based botnet designed for DDoS attacks. Named after the Aqua filename, it was first reported in November 2023.
Security Affairs
JULY 22, 2023
Researchers warn of several DDoS botnets exploiting a critical flaw tracked as CVE-2023-28771 in Zyxel devices. Fortinet FortiGuard Labs researchers warned of multiple DDoS botnets exploiting a vulnerability impacting multiple Zyxel firewalls. Mirai botnets are frequently used to conduct DDoS attacks.”

Security Affairs
JUNE 1, 2023
Threat actors are actively exploiting a command injection flaw, tracked as CVE-2023-28771, in Zyxel firewalls to install malware. Threat actors are actively attempting to exploit a command injection vulnerability, tracked as CVE-2023-28771 , that impacts Zyxel firewalls. in its firewall devices. USG FLEX ZLD V4.60

Security Affairs
JUNE 18, 2023
A collective known as Anonymous Sudan (aka Storm-1359) claimed responsibility for the DDoS attacks that hit the company’s services. Threat actors relied on access to multiple virtual private servers (VPS) in conjunction with rented cloud infrastructure, open proxies, and DDoS tools. ” states SpiderLabs. .”

eSecurity Planet
OCTOBER 11, 2023
Microsoft’s Patch Tuesday for October 2023 covers a total of 103 CVEs, including three zero-day vulnerabilities affecting WordPad, Skype and the HTTP/2 “ Rapid Reset ” DDoS vulnerability. CVE-2023-41763 , an elevation of privilege vulnerability in Skype for Business with a CVSS score of 5.3

Security Affairs
NOVEMBER 17, 2024
that reboots locked devices Ymir ransomware, a new stealthy ransomware grow in the wild Amazon discloses employee data breach after May 2023 MOVEit attacks A new fileless variant of Remcos RAT observed in the wild A surge in Pro-Russia cyberattacks after decision to monitor North Korean Troops in Ukraine U.S.
Security Affairs
APRIL 25, 2023
A flaw in the Service Location Protocol (SLP), tracked as CVE-2023-29552, can allow to carry out powerful DDoS attacks. A high-severity security vulnerability (CVE-2023-29552, CVSS score: 8.6) impacting the Service Location Protocol ( SLP ) can be exploited by threat actors to conduct powerful volumetric DDoS attacks.

SecureWorld News
JUNE 20, 2023
In a Friday blog post, Microsoft blamed a battery of service outages of its Azure, Outlook, and OneDrive platforms in early June on "access to multiple virtual private servers (VPS) in conjunction with rented cloud infrastructure, open proxies, and DDoS tools." It also provides Layer 7 DDoS protection tips. Air Force (Ret.),

The Hacker News
MAY 31, 2023
Tracked as CVE-2023-28771 (CVSS score: 9.8), the issue relates to a command injection flaw impacting different firewall models that could enable an unauthenticated attacker

eSecurity Planet
APRIL 14, 2023
Malicious bots can be used to carry out a range of cyber threats like account takeovers and DDoS attacks, so bot protection is an increasingly important defense for web-facing assets. Bot protection products can also help prevent DDoS attacks. Limited customization options for smaller businesses.

eSecurity Planet
SEPTEMBER 22, 2023
The Barracuda SecureEdge SASE product builds off the well established Barracuda security products (firewalls, gateways, email security, and more) that already protect so many global companies. When compared against other SASE competitors, Barracuda SecureEdge can be considered one of the best options to protect remote users.

eSecurity Planet
SEPTEMBER 25, 2023
Cloudflare also stands out with ZTNA by default, IoT Isolation, and automated traffic controls and anti-DDoS capabilities. Subscribe The post Cloudflare One SASE Review & Features 2023 appeared first on eSecurity Planet. Email Address By signing up to receive our newsletter, you agree to our Terms of Use and Privacy Policy.

CyberSecurity Insiders
MAY 6, 2021
Its website security plans offer SSL Certification that arrives with Web Application Firewall(WAF) protection. Also, the firewall offered by the company blocks all kinds of DDoS and Malware attacks that could damage the website- thus the reputation of the company.

CyberSecurity Insiders
MARCH 24, 2023
The tech giant claims that the activity has occurred for over three months, i.e. between November 2022 and February 2023. Most were distributed denial of service attacks aka DDoS and a mixture of other attack patterns.

eSecurity Planet
DECEMBER 8, 2023
Design robust server architecture to improve redundancy and capacity for resilience against failure or DDoS attacks. Firewalls should be hardened to close unneeded ports. Implement rate limiting to harden against DDoS and DNS tunneling attacks. to help prevent its cache from being poisoned by hackers.

Penetration Testing
JUNE 15, 2025
Allow Remote Root Code Execution via Unauthenticated Attacks Ddos June 16, 2025 Five critical vulnerabilities—each scoring a CVSS of 9.8—have Affected products include BL-WR9000, BL-AC1900, BL-AC2100_AZ3, BL-X10_AC8, BL-X26_AC8, BL-LTE300, BL-F1200_AT1, BLAC450M_AE4, and BL-X26_DA3, across firmware versions dating back to 2023.

Malwarebytes
MAY 15, 2023
This means that Federal Civilian Executive Branch (FCEB) agencies need to remediate these vulnerabilities by June 2, 2023. The Ruckus vulnerability is listed under CVE-2023-25717 , which indicates that Ruckus Wireless Access Point software contains a vulnerability in its web services component.

Security Affairs
JUNE 17, 2023
Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Margaret’s Health is the first hospital to cite a cyberattack as a reason for its closure A database containing data of +8.9

eSecurity Planet
MAY 2, 2024
The 2023 vendor surveys arriving this quarter paint a picture of a cybersecurity landscape under attack, with priority issues affecting deployment, alert response, and exposed vulnerabilities. Sophos: Noted that 43% of all 2023 malware signature updates are for stealers, spyware, and keyloggers often used to steal credentials from devices.

eSecurity Planet
JULY 19, 2023
AWS quotes Reblaze pricing starting at $5,440 a month for comprehensive web application protection, including API, web application firewall and DDoS protection. Read next: Top Application Security Tools & Software The post Top API Security Tools 2023 appeared first on eSecurityPlanet.

Security Affairs
SEPTEMBER 24, 2023
Government of Bermuda blames Russian threat actors for the cyber attack City of Dallas has set a budget of $8.5 Government of Bermuda blames Russian threat actors for the cyber attack City of Dallas has set a budget of $8.5

eSecurity Planet
APRIL 15, 2024
You can strengthen your cybersecurity defenses by using reliable antivirus software, firewalls, intrusion detection systems, and virtual private networks (VPNs). These issues affect over 91,000 exposed machines, putting them at risk of DDoS assaults, account theft, and malware infestations.

eSecurity Planet
JANUARY 30, 2024
Downtime limits incident response, increases the risk of data breaches, and can be used as leverage for DDoS attacks. 8 Common Cloud Storage Security Risks & Mitigations Cloud storage risks include misconfiguration, data breaches, insecure interfaces, DDoS attacks, malware, insider threats, encryption issues, and patching issues.

The Last Watchdog
SEPTEMBER 11, 2023
— Traceable AI, the industry’s leading API security company, today released its comprehensive research report – the 2023 State of API Security: A Global Study on the Reality of API Risk. San Francisco, Calif. Download the full report for in-depth insights and recommendations. 27 at 12 p.m.

Malwarebytes
OCTOBER 31, 2023
BIG-IP is a collection of hardware platforms and software solutions that provides a wide range of services, including load balancing, web application firewall, access control, and DDoS protection. This CVEs is listed as: CVE-2023-46747 ( CVSS score 9.8 F5 provides services focused on security, reliability, and performance.

eSecurity Planet
MAY 24, 2023
A cloud workload protection platform (CWPP) shields cloud workloads from a range of threats like malware, ransomware, DDoS attacks, cloud misconfigurations, insider threats, and data breaches. Read next: 10 Top Cloud Security Companies The post Top 10 Cloud Workload Protection Platforms (CWPP) in 2023 appeared first on eSecurityPlanet.

Security Affairs
APRIL 30, 2023
ViperSoftX uses more sophisticated encryption and anti-analysis techniques Atomic macOS Stealer is advertised on Telegram for $1,000 per month CISA warns of a critical flaw affecting Illumina medical devices OpenAI reinstates ChatGPT service in Italy after meeting Garante Privacy’s demands Cisco discloses a bug in the Prime Collaboration Deployment (..)

Security Affairs
MAY 27, 2023
New Buhti ransomware operation uses rebranded LockBit and Babuk payloads New PowerExchange Backdoor linked to an Iranian APT group Dark Frost Botnet targets the gaming sector with powerful DDoS New CosmicEnergy ICS malware threatens energy grid assets D-Link fixes two critical flaws in D-View 8 network management suite Zyxel firewall and VPN devices (..)

Security Affairs
DECEMBER 15, 2024
CISA adds Cleo Harmony, VLTrader, and LexiCom flaw to its Known Exploited Vulnerabilities catalog German agency BSI sinkholed a botnet of 30,000 devices infected with BadBox U.S.

eSecurity Planet
AUGUST 7, 2024
Network layer: Protects data in transit and ensures safe network paths by utilizing firewalls, VPNs , and secure routing protocols. Application layer: Includes app-level security features such as API, web application firewalls (WAFs) , and endpoint protection to protect user interactions and app data.

eSecurity Planet
AUGUST 11, 2023
Traditional networking either causes operations bottlenecks by forcing all traffic to route through centralized firewalls or exposes remote assets and cloud resources to attack. Equipment and tool reduction: Which existing SD-WAN, firewall, and network security tools will be made redundant by SASE and can be eliminated?

eSecurity Planet
MARCH 14, 2023
When the internet arrived, the network added a firewall to protect networks and users as they connected to the world wide web. Technical controls may be implemented by: Hardware appliances : switches, routers, firewalls, etc. In a complex, modern network, this assumption falls apart.

Thales Cloud Protection & Licensing
OCTOBER 11, 2023
Protect Your Organization from Cybercrime-as-a-Service Attacks madhav Thu, 10/12/2023 - 04:53 In years gone by, only large enterprises needed to be concerned with cybercrime. Cybercriminals can use these botnets to send spam, conduct DDoS attacks, or spread malware.

eSecurity Planet
AUGUST 26, 2022
Whereas older solutions like antivirus, firewalls, and endpoint detection and response (EDR) have long focused on threats at the network perimeter, the intent of NDR is to monitor and act on malicious threats within organization networks using artificial intelligence (AI) and machine learning (ML) analysis.

eSecurity Planet
MARCH 19, 2024
The notable critical vulnerability, CVE-2023-20214 , allows an attacker to bypass authentication validation for the SD-WAN vManage REST API to gain read and limited write permissions to SD-WAN vManage. The vulnerability, CVE-2023-48788 , earns a critical CVSS score of 9.8 Delete these plug-ins from WordPress sites immediately.

eSecurity Planet
FEBRUARY 13, 2023
Controls can be anything from good password hygiene to web application firewalls and internal network segmentation, a layered approach that reduces risk at each step. Web application firewalls (WAF) serve as a barrier to protect applications from various security threats.

Thales Cloud Protection & Licensing
MARCH 6, 2024
Nearly one-third (28%) of all DDoS attacks on APIs focus on financial services organizations, the most targeted industry for this type of attack. In 2023, the leading actor vector was business logic at a staggering 27% of all API attacks. The sheer volume of API traffic gives attackers a larger and more attractive target.

SiteLock
FEBRUARY 15, 2022
Meanwhile, Cisco estimates that the number of distributed denial-of-service (DDoS) attacks will nearly double from 7.8 million in 2023. According to the International Data Corporation, by 2025 nearly 56 billion devices will be connected to the internet throughout the world. million in 2018 to 15.4
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content