Embedding Trust as a Strategic Asset in Technical Leadership
SecureWorld News
NOVEMBER 19, 2024
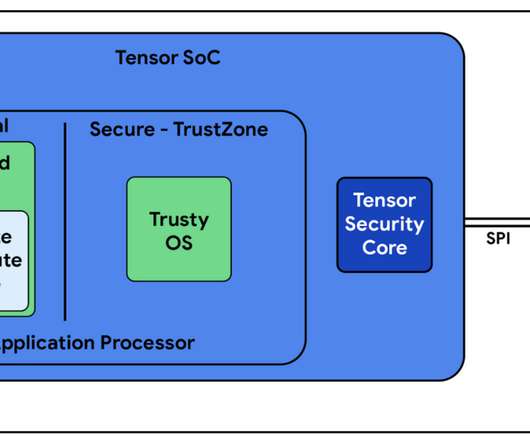
Executive summary Organizations must integrate trust value into their core planning, treating it as a strategic asset that can be manufactured, measured, and managed, much like quality in Total Quality Management. Every day, we manage complex architectures, ensuring each component works together to keep the organization running smoothly.















































Let's personalize your content