Trezor’s Twitter account hijacked by cryptocurrency scammers via bogus Calendly invite
Graham Cluley
MARCH 27, 2024
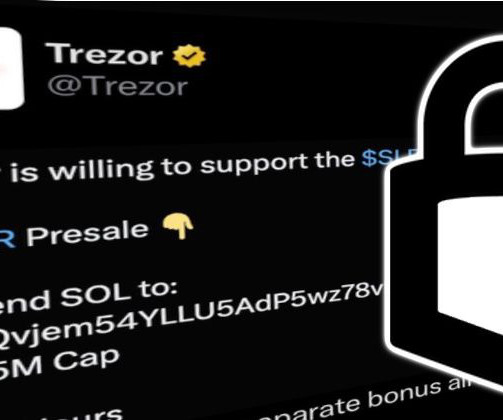
Hardware wallet manufacturer Trezor has explained how its Twitter account was compromised - despite it having sensible security precautions in place, such as strong passwords and multi-factor authentication. Read more in my article on the Hot for Security blog.
















































Let's personalize your content