VPN protocols explained and compared
Malwarebytes
MAY 7, 2021
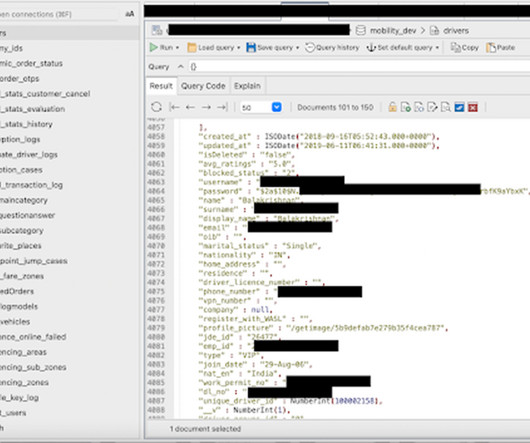
A Virtual Private Network (VPN) creates a safe “tunnel” between you and a computer you trust (normally your VPN provider) to protect your traffic from spying and manipulation. Any VPN worth its money encrypts the information that passes through it, so in this article we will ignore those that don’t use encryption.














































Let's personalize your content