CISA Issues Alert to Secure iPhones Against Pegasus Spyware Zero-Days
SecureWorld News
SEPTEMBER 13, 2023
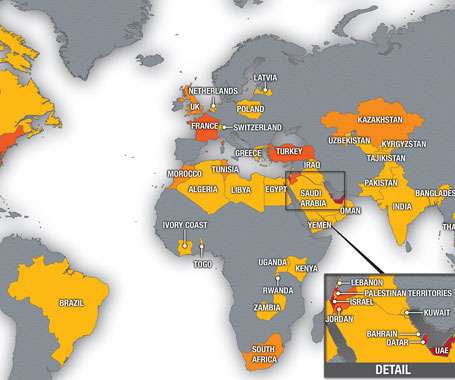
Alarming details have emerged about the exploitation of two Zero-Day vulnerabilities to deploy NSO Group's Pegasus commercial spyware on iPhones. The exploit involved PassKit attachments containing malicious images sent from an attacker iMessage account to the victim." In response to this threat, the U.S.



























Let's personalize your content