Collection #1 Mega Breach Leaks 773 Million Email Accounts
Adam Levin
JANUARY 18, 2019
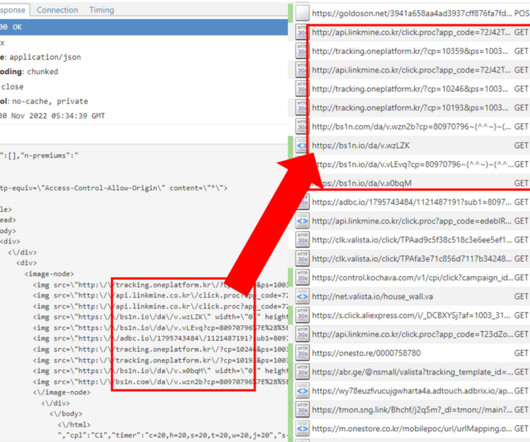
Hunt transferred the compromised emails and passwords to the website haveibeenpwned.com , where users can check to see if their account data was compromised. If this Collection #1 has you spooked, changing your password(s) certainly can’t hurt — unless of course you’re in the habit of re-using passwords. “If










































Let's personalize your content