Lessons From the 2023 National Risk Register Report
IT Security Guru
AUGUST 17, 2023
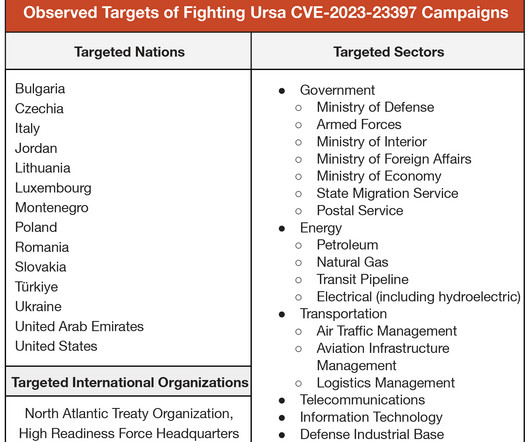
The 2023 Edition of the National Risk Register predicts that, in the next two years, there is a 5 to 25% chance that a devastating attack will target critical infrastructure and cause physical harm. A nationwide loss of power could create a ripple effect, causing disruption to internet telecommunications, water, sewage, fuel and gas supplies.
















































Let's personalize your content