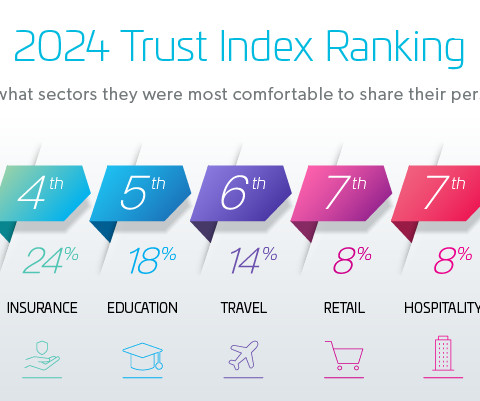
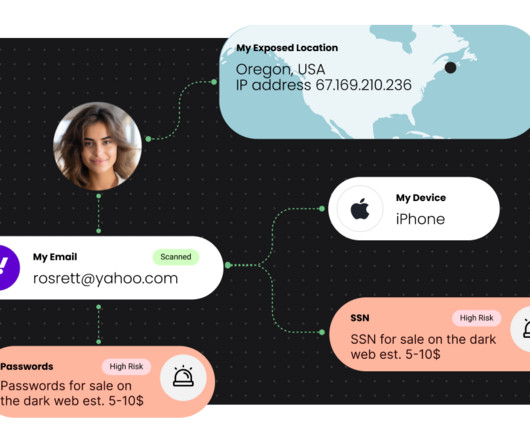
US Senate concerned about Twitter Data Privacy and Security
CyberSecurity Insiders
JUNE 9, 2023
The departure of senior management staff shortly after a change in ownership naturally raises questions about Twitter’s ability to fulfill its legal obligations, particularly with regard to user privacy and data security.





























Let's personalize your content