New Shlayer Mac malware spreads via poisoned search engine results
Security Affairs
JUNE 21, 2020
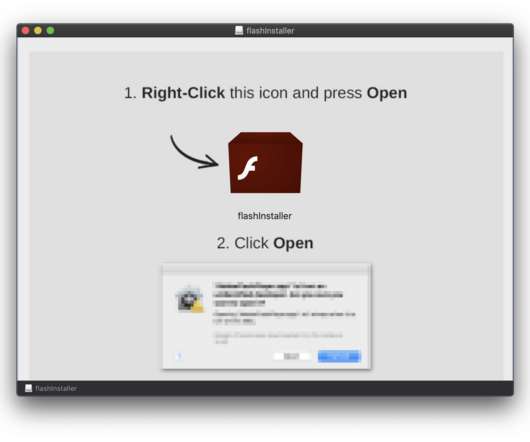
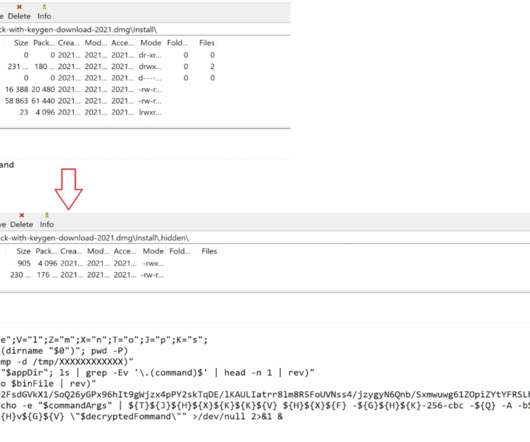
“As of Friday, the new malware installer and its payload had a 0/60 detection rate among all antivirus engines on VirusTotal.” The bash shell script opens and runs itself in the Terminal app, then it extracts a self-embedded, password-protected.zip archive file, which contains a traditional Mac.app bundle. up to 10.14.3.









































Let's personalize your content